diff --git a/Harden-Windows-Security Module/Harden Windows Security.csproj b/Harden-Windows-Security Module/Harden Windows Security.csproj
index 2326e4fcf..5006ab5e6 100644
--- a/Harden-Windows-Security Module/Harden Windows Security.csproj
+++ b/Harden-Windows-Security Module/Harden Windows Security.csproj
@@ -62,11 +62,11 @@
-
+
-
+
diff --git a/Harden-Windows-Security Module/Main files/C#/CimInstances/BitLocker-Enable.cs b/Harden-Windows-Security Module/Main files/C#/CimInstances/BitLocker-Enable.cs
index 91d7cbba9..4864b9dad 100644
--- a/Harden-Windows-Security Module/Main files/C#/CimInstances/BitLocker-Enable.cs
+++ b/Harden-Windows-Security Module/Main files/C#/CimInstances/BitLocker-Enable.cs
@@ -348,8 +348,8 @@ internal static void Enable(string DriveLetter, bool FreePlusUsedSpace)
// Make sure the OS Drive is encrypted first, or else we would add recovery password key protector and then get error about the same problem during auto-unlock key protector enablement
- var volumeInfo = HardenWindowsSecurity.BitLocker.GetEncryptedVolumeInfo(Environment.GetEnvironmentVariable("SystemDrive") ?? "C:\\");
- if (volumeInfo.ProtectionStatus is not BitLocker.ProtectionStatus.Protected)
+ BitLockerVolume OSDriveVolumeInfo = HardenWindowsSecurity.BitLocker.GetEncryptedVolumeInfo(Environment.GetEnvironmentVariable("SystemDrive") ?? "C:\\");
+ if (OSDriveVolumeInfo.ProtectionStatus is not BitLocker.ProtectionStatus.Protected)
{
Logger.LogMessage($"Operation System drive must be encrypted first before encrypting Non-OS drives.", LogTypeIntel.ErrorInteractionRequired);
BitLocker.HasErrorsOccurred = true;
@@ -385,27 +385,52 @@ internal static void Enable(string DriveLetter, bool FreePlusUsedSpace)
#region
// Delete any possible old leftover ExternalKey key protectors
- List ExternalKeys = volumeInfo.KeyProtector!.Where(kp => kp.KeyProtectorType is KeyProtectorType.ExternalKey).ToList();
+ List ExternalKeys = VolumeInfoExtended.KeyProtector!.Where(kp => kp.KeyProtectorType is KeyProtectorType.ExternalKey).ToList();
- if (ExternalKeys.Count > 1)
+ // This step ensures any leftover or unbound external key key protectors will be removed and a working one will be added
+ // If the current one is working and bound, it won't be removed and will be gracefully skipped over.
+ foreach (KeyProtector ExKp in ExternalKeys)
{
- Logger.LogMessage($"The drive {DriveLetter} has more than 1 ExternalKey (Auto-unlock) key protectors, possibly from previous OS installations. Removing all but the one that is currently being used to unlock the drive.", LogTypeIntel.Information);
-
- foreach (KeyProtector ExKp in ExternalKeys)
+ if (ExKp.KeyProtectorID is not null)
{
- if (ExKp.KeyProtectorID is not null)
- {
- RemoveKeyProtector(DriveLetter, ExKp.KeyProtectorID, true);
- }
+ Logger.LogMessage($"Removing ExternalKey key protector with the ID {ExKp.KeyProtectorID} for the drive {DriveLetter}. Will set a new one bound to the OS drive in the next step.", LogTypeIntel.Information);
+
+ RemoveKeyProtector(DriveLetter, ExKp.KeyProtectorID, true);
}
}
+
+
+ // Get the extended volume info based on the drive letter again
+ // Because if the ExternalKey key protectors were deleted in the previous steps,
+ // The extended drive info must be updated to reflect that change
+ VolumeInfoExtended = GetEncryptedVolumeInfo(DriveLetter);
+
+ if (HasErrorsOccurred) { return; }
+
+ // Get the key protectors of the Drive again for the reason mentioned above
+ KeyProtectors = VolumeInfoExtended.KeyProtector!
+ .Select(kp => kp.KeyProtectorType).ToList();
+
+
+ // If the Auto-unlock (aka ExternalKey) key protector is not present, add it
+ // This only runs if all the ExternalKey key protectors were deleted in the previous step
+ // Indicating that none of them were bound to the OS Drive and were leftovers of previous OS Installations
+ if (!KeyProtectors.Contains(BitLocker.KeyProtectorType.ExternalKey))
+ {
+ Logger.LogMessage($"Adding a new {BitLocker.KeyProtectorType.ExternalKey} key protector for Auto-unlock to the drive {DriveLetter}.", LogTypeIntel.Information);
+
+ EnableBitLockerAutoUnlock(DriveLetter);
+
+ if (HasErrorsOccurred) { return; }
+ }
+
#endregion
#region
// Check for presence of multiple recovery password key protectors
- List PasswordProtectors = volumeInfo.KeyProtector!.Where(kp => kp.KeyProtectorType is KeyProtectorType.RecoveryPassword).ToList();
+ List PasswordProtectors = VolumeInfoExtended.KeyProtector!.Where(kp => kp.KeyProtectorType is KeyProtectorType.RecoveryPassword).ToList();
if (PasswordProtectors.Count > 1)
{
@@ -414,6 +439,9 @@ internal static void Enable(string DriveLetter, bool FreePlusUsedSpace)
#endregion
Logger.LogMessage($"The drive {DriveLetter} is fully encrypted with all the required key protectors.", LogTypeIntel.InformationInteractionRequired);
+
+ // Exit the method and do not proceed further if the drive was already encrypted
+ // And key protector checks have been performed
HasErrorsOccurred = true;
return;
}
diff --git a/Harden-Windows-Security Module/Main files/C#/GUI/Protection/EventHandlers.cs b/Harden-Windows-Security Module/Main files/C#/GUI/Protection/EventHandlers.cs
index 3be1f70a8..4c8688038 100644
--- a/Harden-Windows-Security Module/Main files/C#/GUI/Protection/EventHandlers.cs
+++ b/Harden-Windows-Security Module/Main files/C#/GUI/Protection/EventHandlers.cs
@@ -700,10 +700,6 @@ await Task.Run(() =>
case "NonAdminCommands":
{
HardenWindowsSecurity.NonAdminCommands.Invoke();
- if (HardenWindowsSecurity.GUIProtectWinSecurity.SelectedSubCategories.Contains("ClipboardSync"))
- {
- HardenWindowsSecurity.NonAdminCommands.ClipboardSync();
- }
break;
}
diff --git a/Harden-Windows-Security Module/Main files/C#/GUI/Protection/Variables.cs b/Harden-Windows-Security Module/Main files/C#/GUI/Protection/Variables.cs
index 263c62c10..814998abb 100644
--- a/Harden-Windows-Security Module/Main files/C#/GUI/Protection/Variables.cs
+++ b/Harden-Windows-Security Module/Main files/C#/GUI/Protection/Variables.cs
@@ -43,8 +43,7 @@ public partial class GUIProtectWinSecurity
{ "LockScreen", new string[] { "LockScreen_CtrlAltDel", "LockScreen_NoLastSignedIn" } },
{ "UserAccountControl", new string[] { "UAC_NoFastSwitching", "UAC_OnlyElevateSigned" } },
{ "CountryIPBlocking", new string[] { "CountryIPBlocking_OFAC" } },
- { "DownloadsDefenseMeasures", new string[] { "DangerousScriptHostsBlocking" } },
- { "NonAdminCommands", new string[] { "ClipboardSync" } }
+ { "DownloadsDefenseMeasures", new string[] { "DangerousScriptHostsBlocking" } }
};
internal static System.Windows.Controls.ListView? categories;
diff --git a/Harden-Windows-Security Module/Main files/C#/Others/AsyncDownloader.cs b/Harden-Windows-Security Module/Main files/C#/Others/AsyncDownloader.cs
index f6dbb3eff..68b5e09d3 100644
--- a/Harden-Windows-Security Module/Main files/C#/Others/AsyncDownloader.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Others/AsyncDownloader.cs
@@ -17,7 +17,7 @@ public class AsyncDownloader
private static readonly Dictionary fileDictionary = new()
{
{
- "https://download.microsoft.com/download/8/5/C/85C25433-A1B0-4FFA-9429-7E023E7DA8D8/Windows%2011%20v23H2%20Security%20Baseline.zip",
+ "https://download.microsoft.com/download/8/5/C/85C25433-A1B0-4FFA-9429-7E023E7DA8D8/Windows%2011%20v24H2%20Security%20Baseline.zip",
"MicrosoftSecurityBaseline.zip"
},
{
diff --git a/Harden-Windows-Security Module/Main files/C#/Others/Categoriex.cs b/Harden-Windows-Security Module/Main files/C#/Others/Categoriex.cs
index 9f80d776f..b1ee3b2cd 100644
--- a/Harden-Windows-Security Module/Main files/C#/Others/Categoriex.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Others/Categoriex.cs
@@ -19,15 +19,15 @@ public string[] GetValidValues()
"BitLockerSettings", // 21 + conditional item for Hibernation check (only available on non-VMs) + Number of Non-OS drives which are dynamically increased
"TLSSecurity", // 21
"LockScreen", // 14
- "UserAccountControl", // 4
+ "UserAccountControl", // 6
"DeviceGuard", // 8
"WindowsFirewall", // 19
"OptionalWindowsFeatures", // 14
"WindowsNetworking", // 9
"MiscellaneousConfigurations", // 17
- "WindowsUpdateConfigurations", // 14
+ "WindowsUpdateConfigurations", // 15
"EdgeBrowserConfigurations", // 14
- "NonAdminCommands" // 11
+ "NonAdminCommands" // 9
];
return categoriex;
}
diff --git a/Harden-Windows-Security Module/Main files/C#/Others/ConfirmSystemComplianceMethods.cs b/Harden-Windows-Security Module/Main files/C#/Others/ConfirmSystemComplianceMethods.cs
index 5178da294..6e040eec8 100644
--- a/Harden-Windows-Security Module/Main files/C#/Others/ConfirmSystemComplianceMethods.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Others/ConfirmSystemComplianceMethods.cs
@@ -654,6 +654,8 @@ public static Task VerifyBitLockerSettings()
}
else
{
+ HardenWindowsSecurity.Logger.LogMessage("BitLocker is enabled for the OS Drive but it does not conform to the Normal or Enhanced Security levels requirements.", LogTypeIntel.Information);
+
nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
{
FriendlyName = "Secure OS Drive encryption",
@@ -667,6 +669,8 @@ public static Task VerifyBitLockerSettings()
}
else
{
+ HardenWindowsSecurity.Logger.LogMessage("BitLocker is not enabled for the OS Drive.", LogTypeIntel.Information);
+
nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
{
FriendlyName = "Secure OS Drive encryption",
@@ -1856,6 +1860,10 @@ public static Task VerifyMicrosoftDefender()
// Compare the values of the two HashTables if the keys match
foreach (var targetMitigationItem in TargetMitigations)
{
+
+ // Increment the total number of the verifiable compliant values for each process that has a mitigation applied to it in the CSV file
+ HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues++;
+
// Get the current key and value from dictionary containing the CSV data
string ProcessName_Target = targetMitigationItem.Key;
string[] ProcessMitigations_Target = targetMitigationItem.Value;
@@ -1872,31 +1880,52 @@ public static Task VerifyMicrosoftDefender()
// Compare the values of the two dictionaries to see if they are the same without considering the order of the elements (process mitigations)
if (!targetSet.SetEquals(ProcessMitigations_Applied))
{
- // If the values are different, it means the process has different mitigations applied to it than the ones in the CSV file
- HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} were found but are not compliant", LogTypeIntel.Information);
- HardenWindowsSecurity.Logger.LogMessage($"Applied Mitigations: {string.Join(",", ProcessMitigations_Applied)}", LogTypeIntel.Information);
- HardenWindowsSecurity.Logger.LogMessage($"Target Mitigations: {string.Join(",", ProcessMitigations_Target)}", LogTypeIntel.Information);
- // Increment the total number of the verifiable compliant values for each process that has a mitigation applied to it in the CSV file
- HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues++;
+ Logger.LogMessage($"Mitigations for {ProcessName_Target} were found but they do not exactly match, performing further checks", LogTypeIntel.Information);
- nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
+ // Check if the mitigations applied to the current process at least include all of the mitigations required by the CSV file for that process
+ if (ProcessMitigations_Applied.IsSupersetOf(targetSet))
{
- FriendlyName = $"Process Mitigations for: {ProcessName_Target}",
- Compliant = false,
- Value = string.Join(",", ProcessMitigations_Applied),
- Name = $"Process Mitigations for: {ProcessName_Target}",
- Category = CatName,
- Method = "Cmdlet"
- });
+
+ HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} contain all the required mitigations plus more", LogTypeIntel.Information);
+ HardenWindowsSecurity.Logger.LogMessage($"Applied Mitigations: {string.Join(",", ProcessMitigations_Applied)}", LogTypeIntel.Information);
+ HardenWindowsSecurity.Logger.LogMessage($"Target Mitigations: {string.Join(",", ProcessMitigations_Target)}", LogTypeIntel.Information);
+
+ nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
+ {
+ FriendlyName = $"Process Mitigations for: {ProcessName_Target}",
+ Compliant = true,
+ Value = string.Join(",", ProcessMitigations_Target), // Join the array elements into a string to display them properly in the output CSV file
+ Name = $"Process Mitigations for: {ProcessName_Target}",
+ Category = CatName,
+ Method = "Cmdlet"
+ });
+
+ }
+ else
+ {
+
+ HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} do not contain all of the required mitigations", LogTypeIntel.Information);
+ HardenWindowsSecurity.Logger.LogMessage($"Applied Mitigations: {string.Join(",", ProcessMitigations_Applied)}", LogTypeIntel.Information);
+ HardenWindowsSecurity.Logger.LogMessage($"Target Mitigations: {string.Join(",", ProcessMitigations_Target)}", LogTypeIntel.Information);
+
+ nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
+ {
+ FriendlyName = $"Process Mitigations for: {ProcessName_Target}",
+ Compliant = false,
+ Value = string.Join(",", ProcessMitigations_Applied),
+ Name = $"Process Mitigations for: {ProcessName_Target}",
+ Category = CatName,
+ Method = "Cmdlet"
+ });
+
+ }
+
}
else
{
// If the values are the same, it means the process has the same mitigations applied to it as the ones in the CSV file
- HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} are compliant", LogTypeIntel.Information);
-
- // Increment the total number of the verifiable compliant values for each process that has a mitigation applied to it in the CSV file
- HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues++;
+ HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} are precisely compliant and match.", LogTypeIntel.Information);
nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
{
@@ -1914,9 +1943,6 @@ public static Task VerifyMicrosoftDefender()
//If the process name is not found in the HashTable containing the currently applied mitigations, it means the process doesn't have any mitigations applied to it
HardenWindowsSecurity.Logger.LogMessage($"Mitigations for {ProcessName_Target} were not found", LogTypeIntel.Information);
- // Increment the total number of the verifiable compliant values for each process that has a mitigation applied to it in the CSV file
- HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues++;
-
nestedObjectArray.Add(new HardenWindowsSecurity.IndividualResult
{
FriendlyName = $"Process Mitigations for: {ProcessName_Target}",
diff --git a/Harden-Windows-Security Module/Main files/C#/Others/Initializer.cs b/Harden-Windows-Security Module/Main files/C#/Others/Initializer.cs
index af0986779..596c11a51 100644
--- a/Harden-Windows-Security Module/Main files/C#/Others/Initializer.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Others/Initializer.cs
@@ -95,7 +95,7 @@ public static void Initialize(string VerbosePreference = "SilentlyContinue", boo
HardenWindowsSecurity.GlobalVars.MDAVConfigCurrent = HardenWindowsSecurity.ConfigDefenderHelper.GetMpComputerStatus();
// Total number of Compliant values
- HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues = 241;
+ HardenWindowsSecurity.GlobalVars.TotalNumberOfTrueCompliantValues = 242;
// Getting the $VerbosePreference from the calling cmdlet and saving it in the global variable
HardenWindowsSecurity.GlobalVars.VerbosePreference = VerbosePreference;
diff --git a/Harden-Windows-Security Module/Main files/C#/Protect Methods/ClipboardSync.cs b/Harden-Windows-Security Module/Main files/C#/Protect Methods/ClipboardSync.cs
deleted file mode 100644
index d92a17590..000000000
--- a/Harden-Windows-Security Module/Main files/C#/Protect Methods/ClipboardSync.cs
+++ /dev/null
@@ -1,30 +0,0 @@
-using System;
-
-#nullable enable
-
-namespace HardenWindowsSecurity
-{
- public partial class NonAdminCommands
- {
- public static void ClipboardSync()
- {
- if (HardenWindowsSecurity.GlobalVars.path == null)
- {
- throw new System.ArgumentNullException("GlobalVars.path cannot be null.");
- }
-
- HardenWindowsSecurity.Logger.LogMessage("Enabling Clipboard Sync with Microsoft Account", LogTypeIntel.Information);
-
-#nullable disable
- foreach (var Item in (HardenWindowsSecurity.GlobalVars.RegistryCSVItems))
- {
- if (string.Equals(Item.Category, "NonAdmin-ClipboardSync", StringComparison.OrdinalIgnoreCase))
- {
- HardenWindowsSecurity.RegistryEditor.EditRegistry(Item.Path, Item.Key, Item.Value, Item.Type, Item.Action);
- }
- }
-#nullable enable
-
- }
- }
-}
diff --git a/Harden-Windows-Security Module/Main files/C#/Protect Methods/MicrosoftDefender.cs b/Harden-Windows-Security Module/Main files/C#/Protect Methods/MicrosoftDefender.cs
index e5b229562..ddbd5b15f 100644
--- a/Harden-Windows-Security Module/Main files/C#/Protect Methods/MicrosoftDefender.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Protect Methods/MicrosoftDefender.cs
@@ -26,45 +26,15 @@ public static void Invoke()
HardenWindowsSecurity.LGPORunner.RunLGPOCommand(System.IO.Path.Combine(HardenWindowsSecurity.GlobalVars.path, "Resources", "Security-Baselines-X", "Microsoft Defender Policies", "registry.pol"), LGPORunner.FileType.POL);
- HardenWindowsSecurity.Logger.LogMessage("Optimizing Network Protection Performance of the Microsoft Defender", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("AllowSwitchToAsyncInspection", true, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Enabling Real-time protection and Security Intelligence Updates during OOBE", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("OobeEnableRtpAndSigUpdate", true, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Enabling Intel Threat Detection Technology", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("IntelTDTEnabled", true, true);
-
HardenWindowsSecurity.Logger.LogMessage("Enabling Restore point scan", LogTypeIntel.Information);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("DisableRestorePoint", false, true);
- HardenWindowsSecurity.Logger.LogMessage("Disabling Performance mode of Defender that only applies to Dev drives by lowering security", LogTypeIntel.Information);
- // Due to a possible bug or something, 0 means 1 and 1 means 0
- // Invoke-CimMethod -Namespace "ROOT\Microsoft\Windows\Defender" -ClassName "MSFT_MpPreference" -MethodName Set -Arguments @{PerformanceModeStatus = [byte]1}
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("PerformanceModeStatus", 1, true);
+ HardenWindowsSecurity.Logger.LogMessage("Optimizing Network Protection Performance of the Microsoft Defender", LogTypeIntel.Information);
+ HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("AllowSwitchToAsyncInspection", true, true);
HardenWindowsSecurity.Logger.LogMessage("Setting the Network Protection to block network traffic instead of displaying a warning", LogTypeIntel.Information);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("EnableConvertWarnToBlock", true, true);
- //2nd level aggression will come after further testing
- HardenWindowsSecurity.Logger.LogMessage("Setting the Brute-Force Protection to use cloud aggregation to block IP addresses that are over 99% likely malicious", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionAggressiveness", 1, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Setting the Brute-Force Protection to prevent suspicious and malicious behaviors", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionConfiguredState", 1, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Setting the internal feature logic to determine blocking time for the Brute-Force Protections", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionMaxBlockTime", 0, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Setting the Remote Encryption Protection to use cloud intel and context, and block when confidence level is above 90%", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("RemoteEncryptionProtectionAggressiveness", 2, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Setting the Remote Encryption Protection to prevent suspicious and malicious behaviors", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("RemoteEncryptionProtectionConfiguredState", 1, true);
-
- HardenWindowsSecurity.Logger.LogMessage("Setting the internal feature logic to determine blocking time for the Remote Encryption Protection", LogTypeIntel.Information);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("RemoteEncryptionProtectionMaxBlockTime", 0, true);
-
HardenWindowsSecurity.Logger.LogMessage("Extending brute-force protection coverage to block local network addresses.", LogTypeIntel.Information);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionLocalNetworkBlocking", true, true);
diff --git a/Harden-Windows-Security Module/Main files/C#/Protect Methods/OptionalWindowsFeatures.cs b/Harden-Windows-Security Module/Main files/C#/Protect Methods/OptionalWindowsFeatures.cs
index 085a0e6fa..22384f75e 100644
--- a/Harden-Windows-Security Module/Main files/C#/Protect Methods/OptionalWindowsFeatures.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Protect Methods/OptionalWindowsFeatures.cs
@@ -40,7 +40,7 @@ private static void RemoveCapability(string CapabilityIdentity, string Capabilit
string PSScript = $@"
Import-Module -Name 'DISM' -UseWindowsPowerShell -Force -WarningAction SilentlyContinue
$null = Get-WindowsCapability -Online |
-Where-Object -FilterScript {{ $_.Name -eq '{CapabilityIdentity}' }} |
+Where-Object -FilterScript {{ $_.Name -like '*{CapabilityIdentity}*' }} |
Remove-WindowsCapability -Online
";
@@ -123,14 +123,14 @@ public static void Invoke()
ConfigureWindowsOptionalFeature(true, "Containers-DisposableClientVM", "Windows Sandbox", "WindowsSandbox");
ConfigureWindowsOptionalFeature(true, "Microsoft-Hyper-V", "Hyper-V", "HyperV");
- RemoveCapability("Media.WindowsMediaPlayer~~~~0.0.12.0", "The old Windows Media Player");
- RemoveCapability("Browser.InternetExplorer~~~~0.0.11.0", "Internet Explorer Mode for Edge");
- RemoveCapability("WMIC~~~~", "Deprecated WMIC");
- RemoveCapability("Microsoft.Windows.Notepad.System~~~~0.0.1.0", "Old classic Notepad");
- RemoveCapability("Microsoft.Windows.WordPad~~~~0.0.1.0", "Deprecated WordPad");
- RemoveCapability("Microsoft.Windows.PowerShell.ISE~~~~0.0.1.0", "PowerShell ISE");
- RemoveCapability("App.StepsRecorder~~~~0.0.1.0", "Deprecated Steps Recorder");
- RemoveCapability("VBSCRIPT~~~~", "Deprecated VBScript");
+ RemoveCapability("Media.WindowsMediaPlayer", "The old Windows Media Player");
+ RemoveCapability("WMIC", "Deprecated WMIC");
+ RemoveCapability("Microsoft.Windows.Notepad.System", "Old classic Notepad");
+ RemoveCapability("Microsoft.Windows.WordPad", "Deprecated WordPad");
+ RemoveCapability("Microsoft.Windows.PowerShell.ISE", "PowerShell ISE");
+ RemoveCapability("App.StepsRecorder", "Deprecated Steps Recorder");
+ RemoveCapability("VBSCRIPT", "Deprecated VBScript");
+ RemoveCapability("Browser.InternetExplorer", "Internet Explorer Mode for Edge");
}
}
}
diff --git a/Harden-Windows-Security Module/Main files/C#/Unprotect Methods/UnprotectWindowsSecurity.cs b/Harden-Windows-Security Module/Main files/C#/Unprotect Methods/UnprotectWindowsSecurity.cs
index 02cddfbcb..07099cef8 100644
--- a/Harden-Windows-Security Module/Main files/C#/Unprotect Methods/UnprotectWindowsSecurity.cs
+++ b/Harden-Windows-Security Module/Main files/C#/Unprotect Methods/UnprotectWindowsSecurity.cs
@@ -44,7 +44,7 @@ public static void Unprotect()
key?.DeleteSubKeyTree("TLSCipherSuiteDenyList", throwOnMissingSubKey: false);
}
- //Set a tattooed Group policy for SvcHost.exe process mitigations back to disabled state
+ // Set a tattooed Group policy for SvcHost.exe process mitigations back to disabled state
HardenWindowsSecurity.RegistryEditor.EditRegistry(@"HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SCMConfig", "EnableSvchostMitigationPolicy", "0", "DWORD", "AddOrModify");
#endregion
@@ -52,17 +52,9 @@ public static void Unprotect()
#region Advanced Microsoft Defender features
HardenWindowsSecurity.Logger.LogMessage("Reverting the advanced protections in the Microsoft Defender.", LogTypeIntel.Information);
-
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("AllowSwitchToAsyncInspection", false, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("OobeEnableRtpAndSigUpdate", false, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("IntelTDTEnabled", false, true);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("DisableRestorePoint", true, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("PerformanceModeStatus", 0, true);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("EnableConvertWarnToBlock", false, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionAggressiveness", 0, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionConfiguredState", 0, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("RemoteEncryptionProtectionAggressiveness", 0, true);
- HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("RemoteEncryptionProtectionConfiguredState", 0, true);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("BruteForceProtectionLocalNetworkBlocking", false, true);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("EnableEcsConfiguration", false, true);
HardenWindowsSecurity.ConfigDefenderHelper.ManageMpPreference("EngineUpdatesChannel", "0", true);
diff --git a/Harden-Windows-Security Module/Main files/Core/Protect-WindowsSecurity.psm1 b/Harden-Windows-Security Module/Main files/Core/Protect-WindowsSecurity.psm1
index e1c382fb9..e28b5d9c4 100644
--- a/Harden-Windows-Security Module/Main files/Core/Protect-WindowsSecurity.psm1
+++ b/Harden-Windows-Security Module/Main files/Core/Protect-WindowsSecurity.psm1
@@ -284,11 +284,6 @@ Function Protect-WindowsSecurity {
Invoke-Command -ScriptBlock $DynParamCreatorSubCategories -ArgumentList 'DangerousScriptHostsBlocking'
}
- if ('NonAdminCommands' -in $PSBoundParameters['Categories']) {
- # Create a dynamic parameter for -ClipboardSync
- Invoke-Command -ScriptBlock $DynParamCreatorSubCategories -ArgumentList 'ClipboardSync'
- }
-
# Only use the dynamic parameters if the GUI switch is not present
if (-NOT $PSBoundParameters.GUI.IsPresent) {
return $ParamDictionary
@@ -316,7 +311,6 @@ Function Protect-WindowsSecurity {
# Set the default value for LogPath to the current working directory if not specified
New-Variable -Name 'LogPath' -Value $($PSBoundParameters['LogPath'] ?? (Join-Path -Path $(Get-Location).Path -ChildPath "Log-Protect-WindowsSecurity-$(Get-Date -Format 'yyyy-MM-dd HH-mm-ss').txt")) -Force
New-Variable -Name 'DangerousScriptHostsBlocking' -Value $($PSBoundParameters['DangerousScriptHostsBlocking']) -Force
- New-Variable -Name 'ClipboardSync' -Value $($PSBoundParameters['ClipboardSync']) -Force
# Detecting if Offline mode is used
([HardenWindowsSecurity.GlobalVars]::Offline) = $PSBoundParameters['Offline'] ? $true : $false
diff --git a/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/Microsoft.Windows.SDK.NET.dll b/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/Microsoft.Windows.SDK.NET.dll
index 44ae0645d..74844600d 100644
Binary files a/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/Microsoft.Windows.SDK.NET.dll and b/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/Microsoft.Windows.SDK.NET.dll differ
diff --git a/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/WinRT.Runtime.dll b/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/WinRT.Runtime.dll
index 973368c6b..b0c71d5ff 100644
Binary files a/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/WinRT.Runtime.dll and b/Harden-Windows-Security Module/Main files/DLLs/Toast Notifications/WinRT.Runtime.dll differ
diff --git a/Harden-Windows-Security Module/Main files/Harden-Windows-Security-Module.psd1 b/Harden-Windows-Security Module/Main files/Harden-Windows-Security-Module.psd1
index c39c8896f..db0d709b9 100644
--- a/Harden-Windows-Security Module/Main files/Harden-Windows-Security-Module.psd1
+++ b/Harden-Windows-Security Module/Main files/Harden-Windows-Security-Module.psd1
@@ -2,7 +2,7 @@
# https://learn.microsoft.com/en-us/powershell/module/microsoft.powershell.core/about/about_module_manifests
RootModule = 'Harden-Windows-Security-Module.psm1'
- ModuleVersion = '0.6.3'
+ ModuleVersion = '0.6.4'
CompatiblePSEditions = @('Core')
GUID = 'afae7a0a-5eff-4a4d-9139-e1702b7ac426'
Author = 'Violet Hansen'
diff --git a/Harden-Windows-Security Module/Main files/Resources/Default Security Policy.inf b/Harden-Windows-Security Module/Main files/Resources/Default Security Policy.inf
index 1e8d97f74..04f9e8abe 100644
--- a/Harden-Windows-Security Module/Main files/Resources/Default Security Policy.inf
+++ b/Harden-Windows-Security Module/Main files/Resources/Default Security Policy.inf
@@ -17,6 +17,7 @@ MACHINE\System\CurrentControlSet\Control\Print\Providers\LanMan Print Services\S
MACHINE\System\CurrentControlSet\Services\LanmanWorkstation\Parameters\RequireSecuritySignature=4,0
MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdmin=4,5
MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorUser=4,3
+MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\TypeOfAdminApprovalMode=4,1
MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ValidateAdminCodeSignatures=4,0
MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedExactPaths\Machine=7,System\CurrentControlSet\Control\ProductOptions,System\CurrentControlSet\Control\Server Applications,Software\Microsoft\Windows NT\CurrentVersion
MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedPaths\Machine=7,System\CurrentControlSet\Control\Print\Printers,System\CurrentControlSet\Services\Eventlog,Software\Microsoft\OLAP Server,Software\Microsoft\Windows NT\CurrentVersion\Print,Software\Microsoft\Windows NT\CurrentVersion\Windows,System\CurrentControlSet\Control\ContentIndex,System\CurrentControlSet\Control\Terminal Server,System\CurrentControlSet\Control\Terminal Server\UserConfig,System\CurrentControlSet\Control\Terminal Server\DefaultUserConfiguration,Software\Microsoft\Windows NT\CurrentVersion\Perflib,System\CurrentControlSet\Services\SysmonLog
diff --git a/Harden-Windows-Security Module/Main files/Resources/Registry resources.csv b/Harden-Windows-Security Module/Main files/Resources/Registry resources.csv
index 84a3d57a3..014de9203 100644
--- a/Harden-Windows-Security Module/Main files/Resources/Registry resources.csv
+++ b/Harden-Windows-Security Module/Main files/Resources/Registry resources.csv
@@ -115,7 +115,8 @@ Registry Keys,MiscellaneousConfigurations,HKEY_LOCAL_MACHINE,SYSTEM\CurrentContr
Group Policy,MiscellaneousConfigurations,HKEY_LOCAL_MACHINE,Software\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters,EnableCbacAndArmor,Request claims and compound authentication for DAC and Kerberos armoring,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-kerberos#kerberosclientsupportsclaimscompoundarmor
Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,AllowAutoWindowsUpdateDownloadOverMeteredNetwork,Allow updates to be downloaded automatically over metered connections,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautowindowsupdatedownloadovermeterednetwork
Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,AllowTemporaryEnterpriseFeatureControl,Enable features introduced via servicing that are off by default,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowtemporaryenterprisefeaturecontrol
-Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,SetComplianceDeadline,Specify deadlines for automatic updates and restarts,DWORD,1,false,https://learn.microsoft.com/en-us/windows/deployment/update/wufb-compliancedeadlines
+Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,ConfigureDeadlineNoAutoRebootForFeatureUpdates,Specify the number of days before feature updates are installed on devices automatically,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforfeatureupdates
+Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,ConfigureDeadlineNoAutoRebootForQualityUpdates,Specify the number of days before quality updates are installed on devices automatically,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforqualityupdates
Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,ConfigureDeadlineForQualityUpdates,Number of days before quality updates are installed on devices automatically,DWORD,0,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlineforqualityupdates
Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,ConfigureDeadlineGracePeriod,Number of grace period days before quality updates are installed on devices automatically,DWORD,1,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiod
Group Policy,WindowsUpdateConfigurations,HKEY_LOCAL_MACHINE,Software\Policies\Microsoft\Windows\WindowsUpdate,ConfigureDeadlineForFeatureUpdates,Number of days before feature updates are installed on devices automatically,DWORD,0,false,https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlineforfeatureupdates
@@ -146,8 +147,6 @@ Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Windows\Curr
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Control Panel\International\User Profile,HttpAcceptLanguageOptOut,Disable websites accessing local language list,DWORD,1,false,
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings,SafeSearchMode,Turn off safe search in Windows search,DWORD,0,false,
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Clipboard,EnableClipboardHistory,Enable Clipboard History,DWORD,1,false,
-Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Clipboard,CloudClipboardAutomaticUpload,Enable sync of Clipboard history in Windows between devices,DWORD,1,false,
-Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Clipboard,EnableCloudClipboard,Enable Clipboard sync,DWORD,1,false,
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Input\Settings,EnableHwkbTextPrediction,Turn on Show text suggestions when typing on the physical keyboard,DWORD,1,false,
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Software\Microsoft\Input\Settings,MultilingualEnabled,Turn on Multilingual text suggestions,DWORD,1,false,
Registry Keys,NonAdminCommands,HKEY_CURRENT_USER,Control Panel\Accessibility\StickyKeys,Flags,Turn off sticky key shortcut of pressing shift key 5 time fast,String,506,false,
diff --git a/Harden-Windows-Security Module/Main files/Resources/Registry.csv b/Harden-Windows-Security Module/Main files/Resources/Registry.csv
index 97198640b..cc559ea52 100644
--- a/Harden-Windows-Security Module/Main files/Resources/Registry.csv
+++ b/Harden-Windows-Security Module/Main files/Resources/Registry.csv
@@ -47,6 +47,4 @@ NonAdmin,HKEY_CURRENT_USER\Software\Microsoft\Input\Settings,EnableHwkbTextPredi
NonAdmin,HKEY_CURRENT_USER\Software\Microsoft\Input\Settings,MultilingualEnabled,1,DWORD,AddOrModify,turn on Multilingual text suggestions for the current user toggles the option in Windows settings
NonAdmin,HKEY_CURRENT_USER\Control Panel\Accessibility\StickyKeys,Flags,506,String,AddOrModify,turn off sticky key shortcut of pressing shift key 5 time fast
NonAdmin,HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Notifications\Settings,NOC_GLOBAL_SETTING_ALLOW_CRITICAL_TOASTS_ABOVE_LOCK,0,DWORD,AddOrModify,Disables show reminders and incoming VoIP calls on the lock screen in Settings > System > Notifications
-NonAdmin-ClipboardSync,HKEY_CURRENT_USER\Software\Microsoft\Clipboard,EnableClipboardHistory,1,DWORD,AddOrModify,Enable Clipboard History for the current user
-NonAdmin-ClipboardSync,HKEY_CURRENT_USER\Software\Microsoft\Clipboard,CloudClipboardAutomaticUpload,1,DWORD,AddOrModify,2nd commands to enable sync of Clipboard history in Windows between devices
-NonAdmin-ClipboardSync,HKEY_CURRENT_USER\Software\Microsoft\Clipboard,EnableCloudClipboard,1,DWORD,AddOrModify,last one to enable Clipboard sync
\ No newline at end of file
+NonAdmin,HKEY_CURRENT_USER\Software\Microsoft\Clipboard,EnableClipboardHistory,1,DWORD,AddOrModify,Enable Clipboard History for the current user
\ No newline at end of file
diff --git a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Bitlocker Policies/registry.pol b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Bitlocker Policies/registry.pol
index a09453721..8d73804ae 100644
Binary files a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Bitlocker Policies/registry.pol and b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Bitlocker Policies/registry.pol differ
diff --git a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Microsoft Defender Policies/registry.pol b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Microsoft Defender Policies/registry.pol
index 8bd5644b7..1fb59ac3b 100644
Binary files a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Microsoft Defender Policies/registry.pol and b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Microsoft Defender Policies/registry.pol differ
diff --git a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/User Account Control UAC Policies/GptTmpl.inf b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/User Account Control UAC Policies/GptTmpl.inf
index ff0039a86..93d07e66b 100644
Binary files a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/User Account Control UAC Policies/GptTmpl.inf and b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/User Account Control UAC Policies/GptTmpl.inf differ
diff --git a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Windows Update Policies/registry.pol b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Windows Update Policies/registry.pol
index 5b1a43e15..9d2758b47 100644
Binary files a/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Windows Update Policies/registry.pol and b/Harden-Windows-Security Module/Main files/Resources/Security-Baselines-X/Windows Update Policies/registry.pol differ
diff --git a/Harden-Windows-Security Module/Main files/Resources/SecurityPoliciesVerification.csv b/Harden-Windows-Security Module/Main files/Resources/SecurityPoliciesVerification.csv
index e5448c356..98a0da9df 100644
--- a/Harden-Windows-Security Module/Main files/Resources/SecurityPoliciesVerification.csv
+++ b/Harden-Windows-Security Module/Main files/Resources/SecurityPoliciesVerification.csv
@@ -8,8 +8,10 @@ LockScreen,System Access,LockoutBadCount,5,Account lockout threshold
LockScreen,System Access,LockoutDuration,1440,Account lockout duration
LockScreen,System Access,ResetLockoutCount,1440,Reset account lockout counter after
LockScreen,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\DontDisplayLastUserName,"4,1",Interactive logon: Don't display last signed-in
-UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdmin,"4,2",UAC: Behavior of the elevation prompt for administrators in Admin Approval Mode
-UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorUser,"4,0",UAC: Automatically deny elevation requests on Standard accounts
-UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ValidateAdminCodeSignatures,"4,1",UAC: Only elevate executables that are signed and
+UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorAdmin,"4,2",UAC: Behavior of the elevation prompt for administrators in Admin Approval Mode: Prompt for Consent on the Secure Desktop
+UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorUser,"4,1",UAC: Behavior of the elevation prompt for standard users: Prompt for Credentials on the Secure Desktop
+UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ValidateAdminCodeSignatures,"4,1",UAC: Only elevate executables that are signed and Validated
+UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\ConsentPromptBehaviorEnhancedAdmin,"4,1",UAC: Behavior of the elevation prompt for administrators in Enhanced Privilege Protection Mode: Prompt for Credentials on the Secure Desktop
+UserAccountControl,Registry Values,MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System\TypeOfAdminApprovalMode,"4,2",UAC: The type of Admin Approval Mode to be Admin Approval Mode with enhanced privilege protection
WindowsNetworking,Registry Values,MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedExactPaths\Machine,"7,",Network access: Remotely accessible registry paths
WindowsNetworking,Registry Values,MACHINE\System\CurrentControlSet\Control\SecurePipeServers\Winreg\AllowedPaths\Machine,"7,",Network access: Remotely accessible registry paths and subpaths
\ No newline at end of file
diff --git a/Harden-Windows-Security Module/Main files/Resources/XAML/Protect.xaml b/Harden-Windows-Security Module/Main files/Resources/XAML/Protect.xaml
index 6f30b12a9..fc049553f 100644
--- a/Harden-Windows-Security Module/Main files/Resources/XAML/Protect.xaml
+++ b/Harden-Windows-Security Module/Main files/Resources/XAML/Protect.xaml
@@ -214,9 +214,6 @@
-
-
-
diff --git a/Harden-Windows-Security Module/Main files/Shared/HardeningFunctions.ps1 b/Harden-Windows-Security Module/Main files/Shared/HardeningFunctions.ps1
index 351eea211..6c0d89d6c 100644
--- a/Harden-Windows-Security Module/Main files/Shared/HardeningFunctions.ps1
+++ b/Harden-Windows-Security Module/Main files/Shared/HardeningFunctions.ps1
@@ -377,11 +377,6 @@ Function Invoke-NonAdminCommands {
:NonAdminLabel switch ($RunUnattended ? 'Yes' : (Select-Option -Options 'Yes', 'No', 'Exit' -Message "`nRun Non-Admin category ?")) {
'Yes' {
[HardenWindowsSecurity.NonAdminCommands]::Invoke()
- :ClipboardSyncLabel switch ($RunUnattended ? ($ClipboardSync ? 'Yes' : 'No') : (Select-Option -SubCategory -Options 'Yes', 'No' -Message 'Enable Clipboard Syncing with Microsoft Account')) {
- 'Yes' {
- [HardenWindowsSecurity.NonAdminCommands]::ClipboardSync()
- } 'No' { break ClipboardSyncLabel }
- }
# Only suggest restarting the device if Admin related categories were run and the code was not running in unattended mode
if (!$RunUnattended) {
if (!$Categories -and [HardenWindowsSecurity.UserPrivCheck]::IsAdmin()) {
diff --git a/Harden-Windows-Security Module/version.txt b/Harden-Windows-Security Module/version.txt
index a0a15177f..eb514eba8 100644
--- a/Harden-Windows-Security Module/version.txt
+++ b/Harden-Windows-Security Module/version.txt
@@ -1 +1 @@
-0.6.3
\ No newline at end of file
+0.6.4
\ No newline at end of file
diff --git a/README.md b/README.md
index 6d6a1ab61..44aa71c26 100644
--- a/README.md
+++ b/README.md
@@ -246,6 +246,10 @@ From Top to bottom in order:
[Optional Overrides for Microsoft Security Baselines](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Overrides-for-Microsoft-Security-Baseline)
+ +
+
+
+
+
 **Highly recommended** to apply these overrides, the module will ask you whether you want to apply them or not. Use Optional Overrides when applying the hardening measures on Azure VMs.
**Highly recommended** to apply these overrides, the module will ask you whether you want to apply them or not. Use Optional Overrides when applying the hardening measures on Azure VMs.
💡 (back to categories)
@@ -278,23 +282,81 @@ From Top to bottom in order:

--  Enables **additional** security features of Microsoft Defender, You can refer to [this official document](https://docs.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps) for full details.
Enables **additional** security features of Microsoft Defender, You can refer to [this official document](https://docs.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps) for full details.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender)
+-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender)
+-  Extends the [Cloud Security Scan](https://support.microsoft.com/en-us/topic/what-is-a-cloud-security-scan-75112696-7660-4450-9194-d717f72a8ad8) time to the maximum amount of 60 seconds, by default it is 10 seconds. You need to be aware that this means actions like downloading and opening an unknown file **will** make Microsoft Defender send samples of it to the Cloud for more advanced analysis and it can take a maximum of 60 seconds from the time you try to open that unknown file to the time when it will be opened (if deemed safe).
Extends the [Cloud Security Scan](https://support.microsoft.com/en-us/topic/what-is-a-cloud-security-scan-75112696-7660-4450-9194-d717f72a8ad8) time to the maximum amount of 60 seconds, by default it is 10 seconds. You need to be aware that this means actions like downloading and opening an unknown file **will** make Microsoft Defender send samples of it to the Cloud for more advanced analysis and it can take a maximum of 60 seconds from the time you try to open that unknown file to the time when it will be opened (if deemed safe).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudextendedtimeout)
- - [Performance analyzer for Microsoft Defender Antivirus](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/tune-performance-defender-antivirus)
+ - Here is an example of the notification you will see in Windows 11 if that happens.
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudextendedtimeout)
- - [Performance analyzer for Microsoft Defender Antivirus](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/tune-performance-defender-antivirus)
+ - Here is an example of the notification you will see in Windows 11 if that happens.
--  The module makes sure [Cloud Security Scan](https://support.microsoft.com/en-us/topic/what-is-a-cloud-security-scan-75112696-7660-4450-9194-d717f72a8ad8) and [Block At First Sight](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-block-at-first-sight-microsoft-defender-antivirus?view=o365-worldwide#turn-on-block-at-first-sight-with-group-policy) are enabled to the highest possible security states available, **Zero Tolerance Cloud Block level**. You need to be aware that this means actions like downloading and opening an unknown file **will** make Microsoft Defender send samples of it to the Cloud for more advanced analysis and it can take a maximum of 60 seconds (this module sets it to max) from the time you try to open that unknown file to the time when it will be opened (if deemed safe), so you will have to wait. All of these security measures are in place by default in Windows to some extent and happen automatically, but this module **maxes them out and sets them to the highest possible levels**.
The module makes sure [Cloud Security Scan](https://support.microsoft.com/en-us/topic/what-is-a-cloud-security-scan-75112696-7660-4450-9194-d717f72a8ad8) and [Block At First Sight](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-block-at-first-sight-microsoft-defender-antivirus?view=o365-worldwide#turn-on-block-at-first-sight-with-group-policy) are enabled to the highest possible security states available, **Zero Tolerance Cloud Block level**. You need to be aware that this means actions like downloading and opening an unknown file **will** make Microsoft Defender send samples of it to the Cloud for more advanced analysis and it can take a maximum of 60 seconds (this module sets it to max) from the time you try to open that unknown file to the time when it will be opened (if deemed safe), so you will have to wait. All of these security measures are in place by default in Windows to some extent and happen automatically, but this module **maxes them out and sets them to the highest possible levels**.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudblocklevel)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudblocklevel)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudextendedtimeout)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudextendedtimeout)
+ 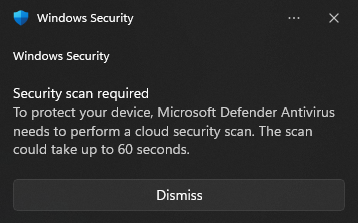
- - Here is an example of the notification you will see in Windows 11 if that happens.
+ -
- 
+
+
+-  Configures the Cloud Block/Protection Level to the **maximum level of Zero Tolerance and [Block At First Sight](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-block-at-first-sight-microsoft-defender-antivirus?view=o365-worldwide#turn-on-block-at-first-sight-with-group-policy)**. No unknown file can run on your system without first being recognized by the Microsoft's Security Graph and other **globally omniscient systems**.
Configures the Cloud Block/Protection Level to the **maximum level of Zero Tolerance and [Block At First Sight](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-block-at-first-sight-microsoft-defender-antivirus?view=o365-worldwide#turn-on-block-at-first-sight-with-group-policy)**. No unknown file can run on your system without first being recognized by the Microsoft's Security Graph and other **globally omniscient systems**.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudblocklevel)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#cloudblocklevel)
+
+ +
+
+
+
+
+-  Configures the Microsoft Defender to send all samples automatically. Increasing protection by participating in the SpyNet / MAPS network.
Configures the Microsoft Defender to send all samples automatically. Increasing protection by participating in the SpyNet / MAPS network.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#submitsamplesconsent)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#submitsamplesconsent)
+
+ +
+
+
+
+
+-  Sets the SpyNet membership to Advanced, improving Cloud Protection.
Sets the SpyNet membership to Advanced, improving Cloud Protection.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowcloudprotection)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowcloudprotection)
+
+ +
+
+
+
-  Enables file hash computation; [designed](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps#-enablefilehashcomputation) to allow admins to force the anti-malware solution to "compute file hashes for every executable file that is scanned if it wasn't previously computed" to "improve blocking for custom indicators in Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).
Enables file hash computation; [designed](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps#-enablefilehashcomputation) to allow admins to force the anti-malware solution to "compute file hashes for every executable file that is scanned if it wasn't previously computed" to "improve blocking for custom indicators in Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#mpengine_enablefilehashcomputation)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#mpengine_enablefilehashcomputation)
+ +
+
+
+
+
-  Clears Quarantined items after 1 day instead of the default behavior of keeping them indefinitely.
Clears Quarantined items after 1 day instead of the default behavior of keeping them indefinitely.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#quarantine_purgeitemsafterdelay)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#quarantine_purgeitemsafterdelay)
+ +
+
+
+
+
-  Allows Microsoft Defender to download security updates even on a metered connection.
Allows Microsoft Defender to download security updates even on a metered connection.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationmeteredconnectionupdates)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationmeteredconnectionupdates)
--  Enables [Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide#settings-and-locations) to scan mapped network drives, network files, [reparse points](https://learn.microsoft.com/en-us/windows/win32/fileio/reparse-points), Emails and removable drives during a full scan.
Enables [Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide#settings-and-locations) to scan mapped network drives, network files, [reparse points](https://learn.microsoft.com/en-us/windows/win32/fileio/reparse-points), Emails and removable drives during a full scan.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowemailscanning)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowemailscanning)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanonmappednetworkdrives)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanonmappednetworkdrives)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanremovabledrivescanning)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanremovabledrivescanning)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablereparsepointscanning)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablereparsepointscanning)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowscanningnetworkfiles)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowscanningnetworkfiles)
+ +
+
+
+
+
+-  Enables Microsoft Defender to scan mapped network drives during full scan.
Enables Microsoft Defender to scan mapped network drives during full scan.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanonmappednetworkdrives)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanonmappednetworkdrives)
+
+ +
+
+
+
+
+-  Enables Microsoft Defender to scan emails. The engine will parse the mailbox and mail files.
Enables Microsoft Defender to scan emails. The engine will parse the mailbox and mail files.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowemailscanning)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowemailscanning)
+
+ +
+
+
+
+
+-  Enables Microsoft Defender to scan Removable Drives.
Enables Microsoft Defender to scan Removable Drives.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanremovabledrivescanning)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowfullscanremovabledrivescanning)
+
+ +
+
+
+
+
+-  Enables Microsoft Defender to scan [Reparse Points](https://learn.microsoft.com/en-us/windows/win32/fileio/reparse-points).
Enables Microsoft Defender to scan [Reparse Points](https://learn.microsoft.com/en-us/windows/win32/fileio/reparse-points).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablereparsepointscanning)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablereparsepointscanning)
+
+ +
+
+
+
+
+-  Forces [Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide#settings-and-locations) to scan network files.
Forces [Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide#settings-and-locations) to scan network files.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowscanningnetworkfiles)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#allowscanningnetworkfiles)
+
+ +
+
+
+
-  Sets the Signature Update Interval to every 3 hours instead of automatically.
Sets the Signature Update Interval to every 3 hours instead of automatically.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#signatureupdateinterval)
@@ -313,16 +375,40 @@ From Top to bottom in order:
@{Engine = $X.versions.engine; Signatures = $X.versions.signatures.'#text'; Platform = $X.versions.platform} | ft -AutoSize
```
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#signatureupdateinterval)
@@ -313,16 +375,40 @@ From Top to bottom in order:
@{Engine = $X.versions.engine; Signatures = $X.versions.signatures.'#text'; Platform = $X.versions.platform} | ft -AutoSize
```
+ +
+
+
+
+
-  Forces Microsoft Defender to check for new virus and spyware definitions before it runs a scan.
Forces Microsoft Defender to check for new virus and spyware definitions before it runs a scan.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#checkforsignaturesbeforerunningscan)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#checkforsignaturesbeforerunningscan)
+ +
+
+
+
+
-  Makes Microsoft Defender run [catch-up scans](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps#-disablecatchupquickscan) for scheduled quick scans. A computer can miss a scheduled scan, usually because the computer is off at the scheduled time, but now after the computer misses two scheduled quick scans, Microsoft Defender runs a catch-up scan the next time someone logs onto the computer.
Makes Microsoft Defender run [catch-up scans](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference?view=windowsserver2022-ps#-disablecatchupquickscan) for scheduled quick scans. A computer can miss a scheduled scan, usually because the computer is off at the scheduled time, but now after the computer misses two scheduled quick scans, Microsoft Defender runs a catch-up scan the next time someone logs onto the computer.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#disablecatchupquickscan)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#disablecatchupquickscan)
+ +
+
+
+
+
-  Enables [Network Protection of Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide)
Enables [Network Protection of Microsoft Defender](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#enablenetworkprotection)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#enablenetworkprotection)
+ +
+
+
+
+
-  Enables [scanning of restore points](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-disablerestorepoint)
Enables [scanning of restore points](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-disablerestorepoint)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablerestorepoint)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_disablerestorepoint)
+ +
+
+
+
+
-  Makes sure [Async Inspection for Network protection](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide#optimizing-network-protection-performance) of Microsoft Defender is turned on - Network protection now has a performance optimization that allows Block mode to start asynchronously inspecting long connections after they're validated and allowed by SmartScreen, which might provide a potential reduction in the cost that inspection has on bandwidth and can also help with app compatibility problems.
Makes sure [Async Inspection for Network protection](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/network-protection?view=o365-worldwide#optimizing-network-protection-performance) of Microsoft Defender is turned on - Network protection now has a performance optimization that allows Block mode to start asynchronously inspecting long connections after they're validated and allowed by SmartScreen, which might provide a potential reduction in the cost that inspection has on bandwidth and can also help with app compatibility problems.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationallowswitchtoasyncinspection)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationallowswitchtoasyncinspection)
+ +
+
+
+
+
- 
 Enables [Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) (*if it's in Evaluation mode*): adds significant protection from new and emerging threats by blocking apps that are malicious or untrusted. Smart App Control also helps to block potentially unwanted apps, which are apps that may cause your device to run slowly, display unexpected ads, offer extra software you didn't want, or do other things you don't expect.
- Smart App Control is User-Mode (and enforces Kernel-Mode) [Windows Defender Application Control policy (WDAC)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/wdac-design-guide), **more info** [**in the Wiki**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction). You can see its status in [System Information](https://support.microsoft.com/en-us/windows/view-your-system-info-a965a8f2-0773-1d65-472a-1e747c9ebe00) and enable it manually from Microsoft Defender app's GUI. It is very important for Windows and Windows Defender intelligence updates to be always up-to-date in order for Smart App Control to work properly as it relies on live intelligence and definition data from the cloud and other sources to make a Smart decision about programs and files it encounters.
@@ -335,12 +421,21 @@ From Top to bottom in order:
- Once you turn Smart App Control off, it can't be turned on without resetting or reinstalling Windows.
--
Enables [Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) (*if it's in Evaluation mode*): adds significant protection from new and emerging threats by blocking apps that are malicious or untrusted. Smart App Control also helps to block potentially unwanted apps, which are apps that may cause your device to run slowly, display unexpected ads, offer extra software you didn't want, or do other things you don't expect.
- Smart App Control is User-Mode (and enforces Kernel-Mode) [Windows Defender Application Control policy (WDAC)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/wdac-design-guide), **more info** [**in the Wiki**](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction). You can see its status in [System Information](https://support.microsoft.com/en-us/windows/view-your-system-info-a965a8f2-0773-1d65-472a-1e747c9ebe00) and enable it manually from Microsoft Defender app's GUI. It is very important for Windows and Windows Defender intelligence updates to be always up-to-date in order for Smart App Control to work properly as it relies on live intelligence and definition data from the cloud and other sources to make a Smart decision about programs and files it encounters.
@@ -335,12 +421,21 @@ From Top to bottom in order:
- Once you turn Smart App Control off, it can't be turned on without resetting or reinstalling Windows.
-- 
 Enables ["Send optional diagnostic data"](https://learn.microsoft.com/en-us/windows/privacy/windows-diagnostic-data) because [it](https://learn.microsoft.com/en-us/windows/privacy/configure-windows-diagnostic-data-in-your-organization) is [required for Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) **to operate when it's in evaluation mode or turned on, and for communication with [Intelligent Security Graph (ISG)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/use-wdac-with-intelligent-security-graph).** You won't see this prompt if Smart App Control is already turned on (this setting will be applied), turned off (this setting will be skipped) or you choose to enable it in the previous step (this setting will be applied).
Enables ["Send optional diagnostic data"](https://learn.microsoft.com/en-us/windows/privacy/windows-diagnostic-data) because [it](https://learn.microsoft.com/en-us/windows/privacy/configure-windows-diagnostic-data-in-your-organization) is [required for Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) **to operate when it's in evaluation mode or turned on, and for communication with [Intelligent Security Graph (ISG)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/use-wdac-with-intelligent-security-graph).** You won't see this prompt if Smart App Control is already turned on (this setting will be applied), turned off (this setting will be skipped) or you choose to enable it in the previous step (this setting will be applied).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-system#allowtelemetry)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-system#allowtelemetry)
+ +
+
+
+
+
+- 
 Enables ["Send optional diagnostic data"](https://learn.microsoft.com/en-us/windows/privacy/windows-diagnostic-data) because [it](https://learn.microsoft.com/en-us/windows/privacy/configure-windows-diagnostic-data-in-your-organization) is [required for Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) **to operate when it's in evaluation mode or turned on, and for communication with [Intelligent Security Graph (ISG)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/use-wdac-with-intelligent-security-graph).** This setting will be automatically applied if Smart App Control is already turned on or you choose to turn it on.
Enables ["Send optional diagnostic data"](https://learn.microsoft.com/en-us/windows/privacy/windows-diagnostic-data) because [it](https://learn.microsoft.com/en-us/windows/privacy/configure-windows-diagnostic-data-in-your-organization) is [required for Smart App Control](https://support.microsoft.com/en-us/topic/what-is-smart-app-control-285ea03d-fa88-4d56-882e-6698afdb7003) **to operate when it's in evaluation mode or turned on, and for communication with [Intelligent Security Graph (ISG)](https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/use-wdac-with-intelligent-security-graph).** This setting will be automatically applied if Smart App Control is already turned on or you choose to turn it on.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-system#allowtelemetry)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-system#allowtelemetry)
+
+ +
+
+
+
-  Enables [Controlled Folder Access](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-controlled-folders). It [helps protect your valuable data](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/controlled-folders) from malicious apps and threats, such as ransomware. Controlled folder access protects your data by checking apps against a list of known, trusted apps. Due to the recent wave of global ransomware attacks, it is important to use this feature to protect your valuables files, specially OneDrive folders.
Enables [Controlled Folder Access](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-controlled-folders). It [helps protect your valuable data](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/controlled-folders) from malicious apps and threats, such as ransomware. Controlled folder access protects your data by checking apps against a list of known, trusted apps. Due to the recent wave of global ransomware attacks, it is important to use this feature to protect your valuables files, specially OneDrive folders.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#enablecontrolledfolderaccess)
- If it blocks a program from accessing one of your folders it protects, and you absolutely trust that program, then you can add it to exclusion list using Microsoft Defender GUI or PowerShell. you can also query the list of allowed apps using PowerShell (commands below). with these commands, you can backup your personalized list of allowed apps, that are relevant to your system, and restore them in case you clean install your Windows.
- -
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#enablecontrolledfolderaccess)
- If it blocks a program from accessing one of your folders it protects, and you absolutely trust that program, then you can add it to exclusion list using Microsoft Defender GUI or PowerShell. you can also query the list of allowed apps using PowerShell (commands below). with these commands, you can backup your personalized list of allowed apps, that are relevant to your system, and restore them in case you clean install your Windows.
- -  The module adds the root of the OneDrive folders of all user accounts present, to the protected folders list of Controlled Folder Access, to provide Ransomware protection for the entire OneDrive folder.
The module adds the root of the OneDrive folders of all user accounts present, to the protected folders list of Controlled Folder Access, to provide Ransomware protection for the entire OneDrive folder.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#controlledfolderaccessprotectedfolders)
+
+ -
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#controlledfolderaccessprotectedfolders)
+
+ -  The root of the OneDrive folders of all the user accounts will be added to the protected folders list of Controlled Folder Access, to provide Ransomware protection for the entire OneDrive folder.
The root of the OneDrive folders of all the user accounts will be added to the protected folders list of Controlled Folder Access, to provide Ransomware protection for the entire OneDrive folder.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#controlledfolderaccessprotectedfolders)
-
```powershell
@@ -354,6 +449,10 @@ From Top to bottom in order:
(Get-MpPreference).ControlledFolderAccessAllowedApplications
```
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#controlledfolderaccessprotectedfolders)
-
```powershell
@@ -354,6 +449,10 @@ From Top to bottom in order:
(Get-MpPreference).ControlledFolderAccessAllowedApplications
```
+ +
+
+
+
+
-  Enables [Mandatory ASLR,](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-exploit-protection?view=o365-worldwide) *It might cause compatibility issues* only for some **poorly-made 3rd party programs**, specially portable ones.
Enables [Mandatory ASLR,](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-exploit-protection?view=o365-worldwide) *It might cause compatibility issues* only for some **poorly-made 3rd party programs**, specially portable ones.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-exploitguard)
- Automatically detects and excludes the Git executables of GitHub Desktop and Git (Standalone version) from mandatory ASLR if they are installed on the system. [More info here](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Git-GitHub-Desktop-and-Mandatory-ASLR)
@@ -362,6 +461,10 @@ From Top to bottom in order:
- `Set-ProcessMitigation -Name "C:\TrustedApp.exe" -Disable ForceRelocateImages`
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-exploitguard)
- Automatically detects and excludes the Git executables of GitHub Desktop and Git (Standalone version) from mandatory ASLR if they are installed on the system. [More info here](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Git-GitHub-Desktop-and-Mandatory-ASLR)
@@ -362,6 +461,10 @@ From Top to bottom in order:
- `Set-ProcessMitigation -Name "C:\TrustedApp.exe" -Disable ForceRelocateImages`
+ +
+
+
+
+
-  Applies [Exploit Protections/Process Mitigations](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-exploit-protection) from [**this list**](https://github.com/HotCakeX/Harden-Windows-Security/blob/main/Harden-Windows-Security%20Module/Main%20files/Resources/ProcessMitigations.csv) to the following programs:
Applies [Exploit Protections/Process Mitigations](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/enable-exploit-protection) from [**this list**](https://github.com/HotCakeX/Harden-Windows-Security/blob/main/Harden-Windows-Security%20Module/Main%20files/Resources/ProcessMitigations.csv) to the following programs:  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-exploitguard)
- All channels of [Microsoft Edge](https://www.microsoft.com/en-us/edge) browser
@@ -376,48 +479,175 @@ From Top to bottom in order:
- Exploit Protection configurations are also accessible in XML format [within this repository](https://github.com/HotCakeX/Harden-Windows-Security/tree/main/Intune%20Files/Hardening%20Policies/Exploit%20Protections). When implementing exploit protections using an XML file, the existing exploit mitigations will seamlessly integrate rather than being overwritten. Should there be pre-existing exploit protections applied to an executable on the system, and the XML file specifies different mitigations for the same executable, these protections will be merged and applied collectively.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-exploitguard)
- All channels of [Microsoft Edge](https://www.microsoft.com/en-us/edge) browser
@@ -376,48 +479,175 @@ From Top to bottom in order:
- Exploit Protection configurations are also accessible in XML format [within this repository](https://github.com/HotCakeX/Harden-Windows-Security/tree/main/Intune%20Files/Hardening%20Policies/Exploit%20Protections). When implementing exploit protections using an XML file, the existing exploit mitigations will seamlessly integrate rather than being overwritten. Should there be pre-existing exploit protections applied to an executable on the system, and the XML file specifies different mitigations for the same executable, these protections will be merged and applied collectively.
+ +
+
+
+
+
-  [Turns on Data Execution Prevention](https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/bcdedit--set) (DEP) for all applications, including 32-bit programs. By default, the output of `BCDEdit /enum "{current}"` (in PowerShell) for the NX bit is `OptIn` but this module sets it to `AlwaysOn`
+
[Turns on Data Execution Prevention](https://learn.microsoft.com/en-us/windows-hardware/drivers/devtest/bcdedit--set) (DEP) for all applications, including 32-bit programs. By default, the output of `BCDEdit /enum "{current}"` (in PowerShell) for the NX bit is `OptIn` but this module sets it to `AlwaysOn`
+ +
+
+
+
+
-  Check for the latest virus and spyware security intelligence on startup.
Check for the latest virus and spyware security intelligence on startup.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_updateonstartup)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_updateonstartup)
+ +
+
+
+
+
-  Specifies the maximum depth to scan archive files to the maximum possible value of `4,294,967,295`
Specifies the maximum depth to scan archive files to the maximum possible value of `4,294,967,295`  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_archivemaxdepth)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#scan_archivemaxdepth)
+ +
+
+
+
+
-  [Defines the maximum size of downloaded files and attachments to be scanned](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide) and set it to the maximum possible value of `10,000,000 KB` or `10 GB`. [the default is](https://github.com/MicrosoftDocs/microsoft-365-docs/pull/5600) `20480 KB` or `~20MB`
[Defines the maximum size of downloaded files and attachments to be scanned](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-advanced-scan-types-microsoft-defender-antivirus?view=o365-worldwide) and set it to the maximum possible value of `10,000,000 KB` or `10 GB`. [the default is](https://github.com/MicrosoftDocs/microsoft-365-docs/pull/5600) `20480 KB` or `~20MB`  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#realtimeprotection_ioavmaxsize)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#realtimeprotection_ioavmaxsize)
--  Enables automatic data collection (formerly known as Capture Threat Window) of [Enhanced Phishing Protection](https://learn.microsoft.com/en-us/windows/security/operating-system-security/virus-and-threat-protection/microsoft-defender-smartscreen/enhanced-phishing-protection) in Microsoft Defender SmartScreen for security analysis from a suspicious website or app.
Enables automatic data collection (formerly known as Capture Threat Window) of [Enhanced Phishing Protection](https://learn.microsoft.com/en-us/windows/security/operating-system-security/virus-and-threat-protection/microsoft-defender-smartscreen/enhanced-phishing-protection) in Microsoft Defender SmartScreen for security analysis from a suspicious website or app.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#automaticdatacollection)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#automaticdatacollection)
+ +
+
+
+
+
+-  Enables the [Enhanced Phishing Protection](https://learn.microsoft.com/en-us/windows/security/operating-system-security/virus-and-threat-protection/microsoft-defender-smartscreen/enhanced-phishing-protection) service.
Enables the [Enhanced Phishing Protection](https://learn.microsoft.com/en-us/windows/security/operating-system-security/virus-and-threat-protection/microsoft-defender-smartscreen/enhanced-phishing-protection) service.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#serviceenabled)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#serviceenabled)
+
+ +
+
+
+
+
+-  Enables notifying user of malicious and phishing scenarios in Microsoft Defender Enhanced Phishing Protection.
Enables notifying user of malicious and phishing scenarios in Microsoft Defender Enhanced Phishing Protection.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifymalicious)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifymalicious)
+
+ +
+
+
+
+
+-  Enables the feature in Enhanced Phishing Protection in Microsoft Defender SmartScreen that warns users if they reuse their work or school password.
Enables the feature in Enhanced Phishing Protection in Microsoft Defender SmartScreen that warns users if they reuse their work or school password.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifypasswordreuse)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifypasswordreuse)
+
+ +
+
+
+
+
+-  Enables warning users if they type their work or school passwords in unsafe apps.
Enables warning users if they type their work or school passwords in unsafe apps.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifyunsafeapp)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#notifyunsafeapp)
+
+ +
+
+
+
+
+-  Enables automatic data collection (formerly known as Capture Threat Window) of Enhanced Phishing Protection in Microsoft Defender SmartScreen for security analysis from a suspicious website or app.
Enables automatic data collection (formerly known as Capture Threat Window) of Enhanced Phishing Protection in Microsoft Defender SmartScreen for security analysis from a suspicious website or app.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#automaticdatacollection)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-webthreatdefense#automaticdatacollection)
+
+ +
+
+
+
+
+- 
 [Creates scheduled task for fast weekly Microsoft recommended driver block list update.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates). You won't see this prompt if the task already exists and is enabled or running.
+
+
[Creates scheduled task for fast weekly Microsoft recommended driver block list update.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates). You won't see this prompt if the task already exists and is enabled or running.
+
+ --
-- 
 [Create scheduled task for fast weekly Microsoft recommended driver block list update.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates). You won't see this prompt if the task already exists and is enabled or running.
+
[Create scheduled task for fast weekly Microsoft recommended driver block list update.](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Fast-and-Automatic-Microsoft-Recommended-Driver-Block-Rules-updates). You won't see this prompt if the task already exists and is enabled or running.
+
- 
 Set Microsoft [Defender engine](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-engineupdateschannel) and [platform update channel](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-platformupdateschannel) to beta.
Set Microsoft [Defender engine](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-engineupdateschannel) and [platform update channel](https://learn.microsoft.com/en-us/powershell/module/defender/set-mppreference#-platformupdateschannel) to beta.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationengineupdateschannel)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationengineupdateschannel)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationplatformupdateschannel)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationplatformupdateschannel)
--  [Defines the number of days before spyware and virus security intelligence definitions](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/manage-outdated-endpoints-microsoft-defender-antivirus?view=o365-worldwide#use-group-policy-to-specify-the-number-of-days-before-protection-is-considered-out-of-date) are considered out of date to 2 days, instead of the default 7 days.
[Defines the number of days before spyware and virus security intelligence definitions](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/manage-outdated-endpoints-microsoft-defender-antivirus?view=o365-worldwide#use-group-policy-to-specify-the-number-of-days-before-protection-is-considered-out-of-date) are considered out of date to 2 days, instead of the default 7 days.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_assignaturedue)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_assignaturedue)
+ +
+
+
+
+
+-  [Defines](https://learn.microsoft.com/en-us/defender-endpoint/manage-outdated-endpoints-microsoft-defender-antivirus?view=o365-worldwide#use-group-policy-to-specify-the-number-of-days-before-protection-is-considered-out-of-date) the number of days before spyware security intelligence is considered out of date to 2. The default is 7.
[Defines](https://learn.microsoft.com/en-us/defender-endpoint/manage-outdated-endpoints-microsoft-defender-antivirus?view=o365-worldwide#use-group-policy-to-specify-the-number-of-days-before-protection-is-considered-out-of-date) the number of days before spyware security intelligence is considered out of date to 2. The default is 7.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_assignaturedue)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_assignaturedue)
+
+ +
+
+
+
+
+-  Defines the number of days before virus security intelligence is considered out of date to 2. The default is 7.
Defines the number of days before virus security intelligence is considered out of date to 2. The default is 7.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_avsignaturedue)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#signatureupdate_avsignaturedue)
+
+ +
+
+
+
-  Sets the [default action](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-remediation-microsoft-defender-antivirus) for Severe and High threat levels to Remove, for Medium and Low threat levels to Quarantine.
Sets the [default action](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/configure-remediation-microsoft-defender-antivirus) for Severe and High threat levels to Remove, for Medium and Low threat levels to Quarantine.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#threats_threatiddefaultaction)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-microsoftdefenderantivirus#threats_threatiddefaultaction)
--  Configures real-time protection and Security Intelligence Updates to be enabled during OOBE.
Configures real-time protection and Security Intelligence Updates to be enabled during OOBE.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationoobeenablertpandsigupdate)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationoobeenablertpandsigupdate)
+ +
+
+
+
+
+-  Configures real-time protection and Security Intelligence Updates to be enabled during OOBE.
Configures real-time protection and Security Intelligence Updates to be enabled during OOBE.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationoobeenablertpandsigupdate)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationoobeenablertpandsigupdate)
--  Enables the [Intel TDT](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-against-ransomware-with-microsoft-defender-for/ba-p/3243941) (Intel® Threat Detection Technology) integration with Microsoft Defender.
Enables the [Intel TDT](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-against-ransomware-with-microsoft-defender-for/ba-p/3243941) (Intel® Threat Detection Technology) integration with Microsoft Defender.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationinteltdtenabled)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationinteltdtenabled)
+ +
+
+
+
+
+-  Enables the [Intel TDT](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-against-ransomware-with-microsoft-defender-for/ba-p/3243941) (Intel® Threat Detection Technology) integration with Microsoft Defender.
Enables the [Intel TDT](https://techcommunity.microsoft.com/t5/microsoft-defender-for-endpoint/defending-against-ransomware-with-microsoft-defender-for/ba-p/3243941) (Intel® Threat Detection Technology) integration with Microsoft Defender.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationinteltdtenabled)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationinteltdtenabled)
+
+ +
+
+
+
--  Disables [Performance Mode](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-antivirus-performance-mode) - [Security risks in relation to Dev Drive](https://learn.microsoft.com/en-us/windows/dev-drive/#understanding-security-risks-and-trust-in-relation-to-dev-drive)
Disables [Performance Mode](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-antivirus-performance-mode) - [Security risks in relation to Dev Drive](https://learn.microsoft.com/en-us/windows/dev-drive/#understanding-security-risks-and-trust-in-relation-to-dev-drive)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationperformancemodestatus)
+-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationperformancemodestatus)
+-  Disables [Performance Mode](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-antivirus-performance-mode) - [Security risks in relation to Dev Drive](https://learn.microsoft.com/en-us/windows/dev-drive/#understanding-security-risks-and-trust-in-relation-to-dev-drive)
Disables [Performance Mode](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-antivirus-performance-mode) - [Security risks in relation to Dev Drive](https://learn.microsoft.com/en-us/windows/dev-drive/#understanding-security-risks-and-trust-in-relation-to-dev-drive)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationperformancemodestatus)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp?WT.mc_id=Portal-fx#configurationperformancemodestatus)
+
+ +
+
+
+
-  Enables a network protection setting that blocks malicious network traffic instead of displaying a warning.
Enables a network protection setting that blocks malicious network traffic instead of displaying a warning.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationenableconvertwarntoblock)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationenableconvertwarntoblock)
--  Configures the Brute-Force Protection to use cloud aggregation to block IP addresses that are over 99% likely malicious
Configures the Brute-Force Protection to use cloud aggregation to block IP addresses that are over 99% likely malicious  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionaggressiveness)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionaggressiveness)
+ +
+
+
+
+
+-  Configures the Brute-Force Protection to use cloud aggregation to block IP addresses that are over 99% likely malicious
Configures the Brute-Force Protection to use cloud aggregation to block IP addresses that are over 99% likely malicious  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionaggressiveness)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionaggressiveness)
+
+ +
+
+
+
+
+-  Configures the Brute-Force Protection to detect and block attempts to forcibly sign in and initiate sessions
Configures the Brute-Force Protection to detect and block attempts to forcibly sign in and initiate sessions  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionconfiguredstate)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionconfiguredstate)
+
+ +
+
+
+
+
+-  Sets the internal feature logic to determine blocking time for the Brute-Force Protections
Sets the internal feature logic to determine blocking time for the Brute-Force Protections  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionmaxblocktime)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionmaxblocktime)
+
+ --
--  Configures the Brute-Force Protection to detect and block attempts to forcibly sign in and initiate sessions
Configures the Brute-Force Protection to detect and block attempts to forcibly sign in and initiate sessions  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionconfiguredstate)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionconfiguredstate)
+
--  Sets the internal feature logic to determine blocking time for the Brute-Force Protections
Sets the internal feature logic to determine blocking time for the Brute-Force Protections  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionmaxblocktime)
+-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionmaxblocktime)
+-  Configures the Remote Encryption Protection to use cloud intel and context, and block when confidence level is above 90%.
Configures the Remote Encryption Protection to use cloud intel and context, and block when confidence level is above 90%.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionaggressiveness)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionaggressiveness)
--  Configures the Remote Encryption Protection to use cloud intel and context, and block when confidence level is above 90%.
Configures the Remote Encryption Protection to use cloud intel and context, and block when confidence level is above 90%.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionaggressiveness)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionaggressiveness)
+ --
--  Configures the Remote Encryption Protection to detect and block attempts to replace local files with encrypted versions from another device
Configures the Remote Encryption Protection to detect and block attempts to replace local files with encrypted versions from another device  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionconfiguredstate)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionconfiguredstate)
+
--  Sets the internal feature logic to determine blocking time for the Remote Encryption Protection
Sets the internal feature logic to determine blocking time for the Remote Encryption Protection  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionmaxblocktime)
+-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionmaxblocktime)
+-  Configures the Remote Encryption Protection to detect and block attempts to replace local files with encrypted versions from another device
Configures the Remote Encryption Protection to detect and block attempts to replace local files with encrypted versions from another device  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionconfiguredstate)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionconfiguredstate)
+
+ +
+
+
+
+
+-  Sets the internal feature logic to determine blocking time for the Remote Encryption Protection
Sets the internal feature logic to determine blocking time for the Remote Encryption Protection  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionmaxblocktime)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksremoteencryptionprotectionremoteencryptionprotectionmaxblocktime)
+
+ +
+
+
+
-  Extends the brute-force protection coverage in the Microsoft Defender Antivirus to block local network addresses.
Extends the brute-force protection coverage in the Microsoft Defender Antivirus to block local network addresses.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionpluginsbruteforceprotectionlocalnetworkblocking)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationbehavioralnetworkblocksbruteforceprotectionbruteforceprotectionpluginsbruteforceprotectionlocalnetworkblocking)
+ +
+
+
+
+
-  Enables [ECS Configurations](https://learn.microsoft.com/en-us/defender-endpoint/microsoft-defender-core-service-configurations-and-experimentation) in the Microsoft Defender. They improve product health and security by *automatically* fixing any possible issues/bugs that may arise, in a timely manner.
+
Enables [ECS Configurations](https://learn.microsoft.com/en-us/defender-endpoint/microsoft-defender-core-service-configurations-and-experimentation) in the Microsoft Defender. They improve product health and security by *automatically* fixing any possible issues/bugs that may arise, in a timely manner.
+ +
+
+
+
+
+-  Enables Network Protection to be configured into block or audit mode on Windows Server.
Enables Network Protection to be configured into block or audit mode on Windows Server.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationallownetworkprotectiononwinserver)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationallownetworkprotectiononwinserver)
+
+ +
+
+
+
+
+> [!TIP]\
+> [Performance analyzer for Microsoft Defender Antivirus](https://learn.microsoft.com/en-us/defender-endpoint/tune-performance-defender-antivirus)
+
💡 (back to categories)
@@ -430,8 +660,6 @@ From Top to bottom in order:

- [Reducing your attack surface](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction) means protecting your devices and network, which leaves attackers with fewer ways to perform attacks. Configuring attack surface reduction rules in Windows can help!
-
[Reducing your attack surface](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction) means protecting your devices and network, which leaves attackers with fewer ways to perform attacks. Configuring attack surface reduction rules in Windows can help!
-
 [Attack surface reduction rules](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide) target certain software behaviors, such as:
[Attack surface reduction rules](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide) target certain software behaviors, such as:  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#attacksurfacereductionrules)
* Launching executable files and scripts that attempt to download or run files
@@ -440,7 +668,10 @@ From Top to bottom in order:
Such software behaviors are sometimes seen in legitimate applications. However, these behaviors are often considered risky because they are commonly abused by attackers through malware. Attack surface reduction rules can constrain software-based risky behaviors and help keep your organization safe.
-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-defender#attacksurfacereductionrules)
* Launching executable files and scripts that attempt to download or run files
@@ -440,7 +668,10 @@ From Top to bottom in order:
Such software behaviors are sometimes seen in legitimate applications. However, these behaviors are often considered risky because they are commonly abused by attackers through malware. Attack surface reduction rules can constrain software-based risky behaviors and help keep your organization safe.
- This module enables [all 19 available Attack Surface Reduction rules shown in the official chart](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#asr-rule-to-guid-matrix).
+[Reducing your attack surface](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction) means protecting your devices and network, which leaves attackers with fewer ways to perform attacks. Configuring attack surface reduction rules in Windows can help!
+
+> [!TIP]\
+> [all 19 available Attack Surface Reduction rules shown in the official chart](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#asr-rule-to-guid-matrix) will be enabled. The Harden Windows Security application also allows you to individually configure each Attack Surface Reduction rule.
This module enables [all 19 available Attack Surface Reduction rules shown in the official chart](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#asr-rule-to-guid-matrix).
+[Reducing your attack surface](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction) means protecting your devices and network, which leaves attackers with fewer ways to perform attacks. Configuring attack surface reduction rules in Windows can help!
+
+> [!TIP]\
+> [all 19 available Attack Surface Reduction rules shown in the official chart](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#asr-rule-to-guid-matrix) will be enabled. The Harden Windows Security application also allows you to individually configure each Attack Surface Reduction rule.
💡 (back to categories)
@@ -483,24 +714,50 @@ Such software behaviors are sometimes seen in legitimate applications. However,
> [!IMPORTANT]\
> [AMD Zen 2 and 3 CPUs have a vulnerability in them](https://github.com/HotCakeX/Harden-Windows-Security/issues/63), if you use one of them, make sure your Bitlocker Startup PIN is at least 16 characters long [*(max is 20)*](https://learn.microsoft.com/en-us/windows/security/operating-system-security/data-protection/bitlocker/bitlocker-group-policy-settings#configure-minimum-pin-length-for-startup).
+ +
+
-  Enables or disables [DMA protection from Bitlocker Countermeasures](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-countermeasures#protecting-thunderbolt-and-other-dma-ports) based [on the status](https://github.com/MicrosoftDocs/windows-itpro-docs/issues/6878#issuecomment-742429128) of [Kernel DMA protection](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt). Kernel DMA Protection is [not compatible](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt#system-compatibility) with other BitLocker DMA attacks countermeasures. It is recommended to disable the BitLocker DMA attacks countermeasures if the system supports Kernel DMA Protection (this module does that exactly). Kernel DMA Protection provides higher security bar for the system over the BitLocker DMA attack countermeasures, while maintaining usability of external peripherals. you can check the status of Kernel DMA protection [using this official guide](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt#how-to-check-if-kernel-dma-protection-is-enabled).
Enables or disables [DMA protection from Bitlocker Countermeasures](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-countermeasures#protecting-thunderbolt-and-other-dma-ports) based [on the status](https://github.com/MicrosoftDocs/windows-itpro-docs/issues/6878#issuecomment-742429128) of [Kernel DMA protection](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt). Kernel DMA Protection is [not compatible](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt#system-compatibility) with other BitLocker DMA attacks countermeasures. It is recommended to disable the BitLocker DMA attacks countermeasures if the system supports Kernel DMA Protection (this module does that exactly). Kernel DMA Protection provides higher security bar for the system over the BitLocker DMA attack countermeasures, while maintaining usability of external peripherals. you can check the status of Kernel DMA protection [using this official guide](https://learn.microsoft.com/en-us/windows/security/information-protection/kernel-dma-protection-for-thunderbolt#how-to-check-if-kernel-dma-protection-is-enabled).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-dataprotection#allowdirectmemoryaccess)
- [Kernel DMA Protection (Memory Access Protection) for OEMs](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-kernel-dma-protection) page shows the requirements for Kernel DMA Protection. for Intel CPUs, support for requirements such as VT-X and VT-D can be found in each CPU's respective product page. e.g. [Intel i7 13700K](https://ark.intel.com/content/www/us/en/ark/products/230500/intel-core-i713700k-processor-30m-cache-up-to-5-40-ghz.html)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-dataprotection#allowdirectmemoryaccess)
- [Kernel DMA Protection (Memory Access Protection) for OEMs](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/oem-kernel-dma-protection) page shows the requirements for Kernel DMA Protection. for Intel CPUs, support for requirements such as VT-X and VT-D can be found in each CPU's respective product page. e.g. [Intel i7 13700K](https://ark.intel.com/content/www/us/en/ark/products/230500/intel-core-i713700k-processor-30m-cache-up-to-5-40-ghz.html)
+ +
+
+
+
+
-  Disallows standard (non-Administrator) users from changing the Bitlocker Startup PIN or password
Disallows standard (non-Administrator) users from changing the Bitlocker Startup PIN or password  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp#systemdrivesdisallowstandarduserscanchangepin)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp#systemdrivesdisallowstandarduserscanchangepin)
+ +
+
+
+
+
-  [Requires you to choose a PIN that contains at least 10 characters](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-group-policy-settings#configure-minimum-pin-length-for-startup)
[Requires you to choose a PIN that contains at least 10 characters](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-group-policy-settings#configure-minimum-pin-length-for-startup)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp#systemdrivesminimumpinlength)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/bitlocker-csp#systemdrivesminimumpinlength)
+ +
+
+
+
+
-  (Only on Physical machines) Enables Hibernate and adds Hibernate to Start menu's power options.
(Only on Physical machines) Enables Hibernate and adds Hibernate to Start menu's power options.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-power#allowhibernate)
- Devices that support [Modern Standby](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/modern-standby) have the most security because [(S1-S3) power states](https://learn.microsoft.com/en-us/windows-hardware/drivers/kernel/system-power-states) which belong to the [legacy sleep modes](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/modern-standby-vs-s3) are not available. In Modern Standby, security components remain vigilant and the OS stays protected. Applying Microsoft Security Baselines also automatically disables the legacy (S1-S3) sleep states.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-power#allowhibernate)
- Devices that support [Modern Standby](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/modern-standby) have the most security because [(S1-S3) power states](https://learn.microsoft.com/en-us/windows-hardware/drivers/kernel/system-power-states) which belong to the [legacy sleep modes](https://learn.microsoft.com/en-us/windows-hardware/design/device-experiences/modern-standby-vs-s3) are not available. In Modern Standby, security components remain vigilant and the OS stays protected. Applying Microsoft Security Baselines also automatically disables the legacy (S1-S3) sleep states.
+ +
+
+
+
+
-  [sets Hibernate to full](https://learn.microsoft.com/en-us/windows/win32/power/system-power-states#hibernation-file-types)
+
[sets Hibernate to full](https://learn.microsoft.com/en-us/windows/win32/power/system-power-states#hibernation-file-types)
+ +
+
+
+
+
-  Enables network connectivity in standby on modern standby-capable systems. This ensures security updates for Microsoft Defender and Windows will be installed automatically.
Enables network connectivity in standby on modern standby-capable systems. This ensures security updates for Microsoft Defender and Windows will be installed automatically.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-power#acconnectivityinstandby_2)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-power#acconnectivityinstandby_2)
+ +
+
+
+
+
-  [Disallows access to Bitlocker-protected removable data drives from earlier versions of Windows.](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-group-policy-settings#allow-access-to-bitlocker-protected-removable-data-drives-from-earlier-versions-of-windows)
Refer to this [official documentation about the countermeasures of Bitlocker](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-countermeasures)
@@ -530,10 +787,22 @@ If you want to read more: [Demystifying Schannel](https://techcommunity.microsof
-
[Disallows access to Bitlocker-protected removable data drives from earlier versions of Windows.](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-group-policy-settings#allow-access-to-bitlocker-protected-removable-data-drives-from-earlier-versions-of-windows)
Refer to this [official documentation about the countermeasures of Bitlocker](https://learn.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-countermeasures)
@@ -530,10 +787,22 @@ If you want to read more: [Demystifying Schannel](https://techcommunity.microsof
-  Disables TLS 1 and TLS 1.1 security protocols that only **exist for backward compatibility**. All modern software should and do use `TLS 1.2` and `TLS 1.3`.
Disables TLS 1 and TLS 1.1 security protocols that only **exist for backward compatibility**. All modern software should and do use `TLS 1.2` and `TLS 1.3`.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#overrideminimumenabledtlsversionclient)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#overrideminimumenabledtlsversionclient)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#overrideminimumenabledtlsversionserver)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#overrideminimumenabledtlsversionserver)
+ +
+
+
+
+
-  Disables [MD5 Hashing Algorithm](https://security.stackexchange.com/questions/52461/how-weak-is-md5-as-a-password-hashing-function) that is **only available for backward compatibility**
+
Disables [MD5 Hashing Algorithm](https://security.stackexchange.com/questions/52461/how-weak-is-md5-as-a-password-hashing-function) that is **only available for backward compatibility**
+ +
+
+
+
+
-  Disables the following [weak ciphers](https://github.com/ssllabs/research/wiki/SSL-and-TLS-Deployment-Best-Practices) that are **only available for backward compatibility**: `"DES 56-bit"`,`"RC2 40-bit"`,`"RC2 56-bit"`,`"RC2 128-bit"`,`"RC4 40-bit"`,`"RC4 56-bit"`,`"RC4 64-bit"`,`"RC4 128-bit"`,`"3DES 168-bit (Triple DES 168)"`
+
Disables the following [weak ciphers](https://github.com/ssllabs/research/wiki/SSL-and-TLS-Deployment-Best-Practices) that are **only available for backward compatibility**: `"DES 56-bit"`,`"RC2 40-bit"`,`"RC2 56-bit"`,`"RC2 128-bit"`,`"RC4 40-bit"`,`"RC4 56-bit"`,`"RC4 64-bit"`,`"RC4 128-bit"`,`"3DES 168-bit (Triple DES 168)"`
+ +
+
+
+
+
-  Configures the [TLS](https://www.ncsc.gov.uk/guidance/using-tls-to-protect-data) to only use the [following](https://developers.cloudflare.com/ssl/reference/cipher-suites/recommendations/) secure [cipher suites](https://learn.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-11) and in this [exact](https://scanigma.com/knowledge-base) order:
Configures the [TLS](https://www.ncsc.gov.uk/guidance/using-tls-to-protect-data) to only use the [following](https://developers.cloudflare.com/ssl/reference/cipher-suites/recommendations/) secure [cipher suites](https://learn.microsoft.com/en-us/windows/win32/secauthn/tls-cipher-suites-in-windows-11) and in this [exact](https://scanigma.com/knowledge-base) order:  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#tlsciphersuites)
```
@@ -548,6 +817,10 @@ TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
```
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#tlsciphersuites)
```
@@ -548,6 +817,10 @@ TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
```
+ +
+
+
+
+
-  [Configures](https://learn.microsoft.com/en-us/windows-server/security/tls/manage-tls) TLS ECC Curves to [use the following](https://github.com/HotCakeX/Harden-Windows-Security/commit/5b5be1fcab8f7bf5d364f48459aecfc54c6eff9d#commitcomment-115982586) prioritized Curves order:
[Configures](https://learn.microsoft.com/en-us/windows-server/security/tls/manage-tls) TLS ECC Curves to [use the following](https://github.com/HotCakeX/Harden-Windows-Security/commit/5b5be1fcab8f7bf5d364f48459aecfc54c6eff9d#commitcomment-115982586) prioritized Curves order:  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#configureellipticcurvecryptography)
```
@@ -583,26 +856,58 @@ NistP384
-
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-cryptography#configureellipticcurvecryptography)
```
@@ -583,26 +856,58 @@ NistP384
-  [Automatically locks device after X seconds of inactivity](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-inactivity-limit) (just like mobile phones), which is set to 120 seconds (2 minutes) in this module, you can change that to any value you like.
[Automatically locks device after X seconds of inactivity](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-inactivity-limit) (just like mobile phones), which is set to 120 seconds (2 minutes) in this module, you can change that to any value you like.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_machineinactivitylimit)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_machineinactivitylimit)
+ +
+
+
+
+
- 
 [Requires **CTRL+ALT+DEL** on the lock screen](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-do-not-require-ctrl-alt-del), kernel protected set of key strokes. The reason and logic behind it is:
[Requires **CTRL+ALT+DEL** on the lock screen](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-do-not-require-ctrl-alt-del), kernel protected set of key strokes. The reason and logic behind it is:  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotrequirectrlaltdel)
- A malicious user might install malware that looks like the standard sign-in dialog box for the Windows operating system and capture a user's password. The attacker can then sign into the compromised account with whatever level of user rights that user has.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotrequirectrlaltdel)
- A malicious user might install malware that looks like the standard sign-in dialog box for the Windows operating system and capture a user's password. The attacker can then sign into the compromised account with whatever level of user rights that user has.
+ +
+
+
+
+
-  Enables [a security anti-hammering feature](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-account-lockout-threshold) that sets a threshold of **5** for the number of failed sign-in attempts that causes the device to be locked by using BitLocker. Sign-in attempts include Windows password or Windows Hello authentication methods. This threshold means, if the specified maximum number of failed sign-in attempts is exceeded, the device will invalidate the Trusted Platform Module (TPM) protector and any other protector except the 48-digit recovery password, and then reboot. During Device Lockout mode, the computer or device only boots into the touch-enabled Windows Recovery Environment (WinRE) until an authorized user enters the recovery password to restore full access.
- This module (in the Bitlocker category) automatically saves the 48-digit recovery password of each drive in itself, the location of it will also be visible on the PowerShell console when you run it. It is **very important to keep it in a safe and reachable place, e.g. in OneDrive's Personal Vault which requires authentication to access. See [Here](https://www.microsoft.com/en-us/microsoft-365/onedrive/personal-vault) and [Here](https://support.microsoft.com/en-us/office/protect-your-onedrive-files-in-personal-vault-6540ef37-e9bf-4121-a773-56f98dce78c4) for more info about OneDrive's Personal Vault**
+
Enables [a security anti-hammering feature](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-machine-account-lockout-threshold) that sets a threshold of **5** for the number of failed sign-in attempts that causes the device to be locked by using BitLocker. Sign-in attempts include Windows password or Windows Hello authentication methods. This threshold means, if the specified maximum number of failed sign-in attempts is exceeded, the device will invalidate the Trusted Platform Module (TPM) protector and any other protector except the 48-digit recovery password, and then reboot. During Device Lockout mode, the computer or device only boots into the touch-enabled Windows Recovery Environment (WinRE) until an authorized user enters the recovery password to restore full access.
- This module (in the Bitlocker category) automatically saves the 48-digit recovery password of each drive in itself, the location of it will also be visible on the PowerShell console when you run it. It is **very important to keep it in a safe and reachable place, e.g. in OneDrive's Personal Vault which requires authentication to access. See [Here](https://www.microsoft.com/en-us/microsoft-365/onedrive/personal-vault) and [Here](https://support.microsoft.com/en-us/office/protect-your-onedrive-files-in-personal-vault-6540ef37-e9bf-4121-a773-56f98dce78c4) for more info about OneDrive's Personal Vault**
+ +
+
+
+
+
-  Configures account lockout policy: [Account lockout threshold](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account-lockout-threshold), Sets the number of allowed failed sign-in attempts to **5**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked. **This policy greatly prevents brute force attempts.**
Configures account lockout policy: [Account lockout threshold](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account-lockout-threshold), Sets the number of allowed failed sign-in attempts to **5**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked. **This policy greatly prevents brute force attempts.**  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+ +
+
+
+
+
-  Configures account lockout policy: Sets [Account lockout duration](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account-lockout-duration) to **1440 minutes or 1 day**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked.
Configures account lockout policy: Sets [Account lockout duration](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/account-lockout-duration) to **1440 minutes or 1 day**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+ +
+
+
+
+
-  Configures account lockout policy: Sets [Reset account lockout counter](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/reset-account-lockout-counter-after) to **1440 minutes or 1 day**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked.
Configures account lockout policy: Sets [Reset account lockout counter](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/reset-account-lockout-counter-after) to **1440 minutes or 1 day**. In combination with other policies in this category, this means every 5 failed sign-in attempts will need a full day to pass before 5 more attempts can be made, otherwise Bitlocker will engage, system will be restarted and 48-digit Bitlocker code will be asked.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-devicelock#accountlockoutpolicy)
+ +
+
+
+
+
-  [Hides email address of the Microsoft account on lock screen](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-display-user-information-when-the-session-is-locked), if your device is in a trusted place like at home then this isn't necessary.
+
[Hides email address of the Microsoft account on lock screen](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-display-user-information-when-the-session-is-locked), if your device is in a trusted place like at home then this isn't necessary.
+ +
+
+
+
+
-  [Don't display username at sign-in](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-dont-display-username-at-sign-in); If a user signs in as Other user, the full name of the user isn't displayed during sign-in. In the same context, if users type their email address and password at the sign-in screen and press Enter, the displayed text "Other user" remains unchanged, and is no longer replaced by the user's first and last name, as in previous versions of Windows 10. Additionally, if users enter their domain user name and password and click Submit, their full name isn't shown until the Start screen displays.
[Don't display username at sign-in](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-dont-display-username-at-sign-in); If a user signs in as Other user, the full name of the user isn't displayed during sign-in. In the same context, if users type their email address and password at the sign-in screen and press Enter, the displayed text "Other user" remains unchanged, and is no longer replaced by the user's first and last name, as in previous versions of Windows 10. Additionally, if users enter their domain user name and password and click Submit, their full name isn't shown until the Start screen displays.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotdisplayusernameatsignin)
- [Useful](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-dont-display-username-at-sign-in#best-practices) If you have devices that store sensitive data, with monitors displayed in unsecured locations, or if you have devices with sensitive data that are remotely accessed, revealing logged on user's full names or domain account names
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotdisplayusernameatsignin)
- [Useful](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-dont-display-username-at-sign-in#best-practices) If you have devices that store sensitive data, with monitors displayed in unsecured locations, or if you have devices with sensitive data that are remotely accessed, revealing logged on user's full names or domain account names
+ +
+
+
+
+
- 
 [Don't display last signed-in](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-do-not-display-last-user-name); This security policy setting determines whether the name of the last user to sign in to the device is displayed on the Secure Desktop. If this policy is enabled, the full name of the last user to successfully sign in isn't displayed on the Secure Desktop, nor is the user's sign-in tile displayed. Additionally, if the Switch user feature is used, the full name and sign-in tile aren't displayed. The sign-in screen requests both Username + Windows Hello credentials.
[Don't display last signed-in](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/interactive-logon-do-not-display-last-user-name); This security policy setting determines whether the name of the last user to sign in to the device is displayed on the Secure Desktop. If this policy is enabled, the full name of the last user to successfully sign in isn't displayed on the Secure Desktop, nor is the user's sign-in tile displayed. Additionally, if the Switch user feature is used, the full name and sign-in tile aren't displayed. The sign-in screen requests both Username + Windows Hello credentials.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotdisplaylastsignedin)
- This feature can be useful to enable if you live in *High-Risk Environments* and you don't want anyone to get any information about your accounts when you aren't logged-in.
@@ -611,18 +916,26 @@ NistP384
- If you use Windows Hello Face or Fingerprint, you can easily login using those credential providers without the need to supply username first.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#interactivelogon_donotdisplaylastsignedin)
- This feature can be useful to enable if you live in *High-Risk Environments* and you don't want anyone to get any information about your accounts when you aren't logged-in.
@@ -611,18 +916,26 @@ NistP384
- If you use Windows Hello Face or Fingerprint, you can easily login using those credential providers without the need to supply username first.
+ +
+
+
+
+
-  [Don't Display Network Selection UI on Lock Screen](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#dontdisplaynetworkselectionui) (like WIFI Icon); This setting allows you to control whether anyone can interact with available networks UI on the logon screen. Once enabled, the device's network connectivity state cannot be changed without signing into Windows. Suitable for *High-Risk Environments*.
[Don't Display Network Selection UI on Lock Screen](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#dontdisplaynetworkselectionui) (like WIFI Icon); This setting allows you to control whether anyone can interact with available networks UI on the logon screen. Once enabled, the device's network connectivity state cannot be changed without signing into Windows. Suitable for *High-Risk Environments*.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#dontdisplaynetworkselectionui)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#dontdisplaynetworkselectionui)
+ +
+
+
+
+
-  Applies the following [PIN Complexity rules](https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization#pin-complexity) to Windows Hello
Applies the following [PIN Complexity rules](https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/hello-manage-in-organization#pin-complexity) to Windows Hello  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexity). Please note that, by default, any character can be set as a PIN. However, the following policies ensure that certain characters are always included as a minimum requirement.
- [Must include digits](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexitydigits)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexity). Please note that, by default, any character can be set as a PIN. However, the following policies ensure that certain characters are always included as a minimum requirement.
- [Must include digits](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexitydigits)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexitydigits)
-
+
- [Expires](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexityexpiration) **every 180 days** (default behavior is to never expire)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexitydigits)
-
+
- [Expires](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexityexpiration) **every 180 days** (default behavior is to never expire)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexityexpiration)
-
+
- Setting an expiration date ensures that, in the event of theft, a threat actor cannot indefinitely attempt to guess the PIN. After 180 days, the PIN expires, rendering it unusable even if guessed correctly. To reset the PIN, authentication via a Microsoft account or EntraID—likely inaccessible to the attacker—will be required. Combined with anti-hammering and BitLocker policies, this expiration guarantees that a threat actor cannot endlessly persist in guessing the PIN.
-
+
- [History](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexityhistory) of the **1** most recent selected PIN is preserved to prevent the user from reusing it
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexityexpiration)
-
+
- Setting an expiration date ensures that, in the event of theft, a threat actor cannot indefinitely attempt to guess the PIN. After 180 days, the PIN expires, rendering it unusable even if guessed correctly. To reset the PIN, authentication via a Microsoft account or EntraID—likely inaccessible to the attacker—will be required. Combined with anti-hammering and BitLocker policies, this expiration guarantees that a threat actor cannot endlessly persist in guessing the PIN.
-
+
- [History](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexityhistory) of the **1** most recent selected PIN is preserved to prevent the user from reusing it  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexityhistory)
-
+
- [Must include lower-case letters](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexitylowercaseletters)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexityhistory)
-
+
- [Must include lower-case letters](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#usertenantidpoliciespincomplexitylowercaseletters)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexitylowercaseletters)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/passportforwork-csp#devicetenantidpoliciespincomplexitylowercaseletters)
💡 (back to categories)
@@ -641,15 +954,36 @@ NistP384
-  [Prompt for elevation of privilege on secure desktop for all binaries](https://learn.microsoft.com/en-us/windows/security/identity-protection/user-account-control/user-account-control-group-policy-and-registry-key-settings#user-account-control-behavior-of-the-elevation-prompt-for-administrators-in-admin-approval-mode) in [Administrator accounts](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-gpsb/341747f5-6b5d-4d30-85fc-fa1cc04038d4), which presents the sign-in UI and restricts functionality and access to the system until the sign-in requirements are satisfied. The [secure desktop's](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-switch-to-the-secure-desktop-when-prompting-for-elevation#reference) primary difference from the user desktop is that only trusted processes running as SYSTEM are allowed to run here (that is, nothing is running at the user's privilege level). The path to get to the secure desktop from the user desktop must also be trusted through the entire chain.
[Prompt for elevation of privilege on secure desktop for all binaries](https://learn.microsoft.com/en-us/windows/security/identity-protection/user-account-control/user-account-control-group-policy-and-registry-key-settings#user-account-control-behavior-of-the-elevation-prompt-for-administrators-in-admin-approval-mode) in [Administrator accounts](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-gpsb/341747f5-6b5d-4d30-85fc-fa1cc04038d4), which presents the sign-in UI and restricts functionality and access to the system until the sign-in requirements are satisfied. The [secure desktop's](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-switch-to-the-secure-desktop-when-prompting-for-elevation#reference) primary difference from the user desktop is that only trusted processes running as SYSTEM are allowed to run here (that is, nothing is running at the user's privilege level). The path to get to the secure desktop from the user desktop must also be trusted through the entire chain.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_behavioroftheelevationpromptforadministrators)
- - **This is the default behavior:** prompt the administrator in Admin Approval Mode to select either "Permit" or "Deny" for an operation that requires elevation of privilege for any non-Windows binaries. If the Consent Admin selects Permit, the operation will continue with the highest available privilege. This operation will happen on the secure desktop
- - **This is the behavior that this module sets:** prompts the administrator in Admin Approval Mode to select either "Permit" or "Deny" an operation that requires elevation of privilege. If the Consent Admin selects Permit, the operation will continue with the highest available privilege. "Prompt for consent" removes the inconvenience of requiring that users enter their name and password to perform a privileged task. This operation occurs on the secure desktop.
+ - **Default Behavior:** Prompt for consent for non-Windows binaries: When an operation for a non-Microsoft application requires elevation of privilege, the user is prompted on the secure desktop to select either Permit or Deny. If the user selects Permit, the operation continues with the user's highest available privilege.
+
+ - **Harden Windows Security Behavior:** When an operation requires elevation of privilege, the user is prompted on the secure desktop to select either Permit or Deny. If the user selects Permit, the operation continues with the user's highest available privilege.
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_behavioroftheelevationpromptforadministrators)
- - **This is the default behavior:** prompt the administrator in Admin Approval Mode to select either "Permit" or "Deny" for an operation that requires elevation of privilege for any non-Windows binaries. If the Consent Admin selects Permit, the operation will continue with the highest available privilege. This operation will happen on the secure desktop
- - **This is the behavior that this module sets:** prompts the administrator in Admin Approval Mode to select either "Permit" or "Deny" an operation that requires elevation of privilege. If the Consent Admin selects Permit, the operation will continue with the highest available privilege. "Prompt for consent" removes the inconvenience of requiring that users enter their name and password to perform a privileged task. This operation occurs on the secure desktop.
+ - **Default Behavior:** Prompt for consent for non-Windows binaries: When an operation for a non-Microsoft application requires elevation of privilege, the user is prompted on the secure desktop to select either Permit or Deny. If the user selects Permit, the operation continues with the user's highest available privilege.
+
+ - **Harden Windows Security Behavior:** When an operation requires elevation of privilege, the user is prompted on the secure desktop to select either Permit or Deny. If the user selects Permit, the operation continues with the user's highest available privilege.
+
+ +
+
+
+
- 
 Only elevate executables that are signed and validated [by enforcing cryptographic signatures on any interactive application](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-only-elevate-executables-that-are-signed-and-validated) that requests elevation of privilege. One of the [Potential impacts](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-only-elevate-executables-that-are-signed-and-validated#potential-impact) of it is that it can prevent certain poorly designed programs from prompting for UAC.
Only elevate executables that are signed and validated [by enforcing cryptographic signatures on any interactive application](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-only-elevate-executables-that-are-signed-and-validated) that requests elevation of privilege. One of the [Potential impacts](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/user-account-control-only-elevate-executables-that-are-signed-and-validated#potential-impact) of it is that it can prevent certain poorly designed programs from prompting for UAC.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_onlyelevateexecutablefilesthataresignedandvalidated)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_onlyelevateexecutablefilesthataresignedandvalidated)
+ +
+
+
+
+
- 
 Hides the entry points for [Fast User Switching](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon).
Hides the entry points for [Fast User Switching](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon).  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#hidefastuserswitching)
- This policy will prevent you from using "Forgot my PIN" feature in lock screen or logon screen. If you forget your PIN, you won't be able to recover it.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-windowslogon#hidefastuserswitching)
- This policy will prevent you from using "Forgot my PIN" feature in lock screen or logon screen. If you forget your PIN, you won't be able to recover it.
+ +
+
+
+
+
+-  Sets the behavior of the elevation prompt for Standard users to Prompt for Credentials on the Secure Desktop.
Sets the behavior of the elevation prompt for Standard users to Prompt for Credentials on the Secure Desktop.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_behavioroftheelevationpromptforstandardusers)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-localpoliciessecurityoptions#useraccountcontrol_behavioroftheelevationpromptforstandardusers)
+
+ +
+
+
+
+
+-  Configures the type of [Admin Approval Mode](https://techcommunity.microsoft.com/t5/microsoft-security-baselines/windows-11-version-24h2-security-baseline/ba-p/4252801) to be Admin Approval Mode with enhanced privilege protection.
+
Configures the type of [Admin Approval Mode](https://techcommunity.microsoft.com/t5/microsoft-security-baselines/windows-11-version-24h2-security-baseline/ba-p/4252801) to be Admin Approval Mode with enhanced privilege protection.
+
💡 (back to categories)
@@ -666,10 +1000,22 @@ NistP384
-  Makes sure Windows Firewall is enabled for all profiles (which is the default)
Makes sure Windows Firewall is enabled for all profiles (which is the default)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofileenablefirewall)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofileenablefirewall)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofileenablefirewall)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofileenablefirewall)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofileenablefirewall)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofileenablefirewall)
+ +
+
+
+
+
-  Sets inbound and outbound default actions for Domain Firewall Profile to Block; because this module is Not intended to be used on devices that are part of a domain or controlled by an Active Directory Domain Controller, since they will have their own policies and policy management systems in place.
Sets inbound and outbound default actions for Domain Firewall Profile to Block; because this module is Not intended to be used on devices that are part of a domain or controlled by an Active Directory Domain Controller, since they will have their own policies and policy management systems in place.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofiledefaultinboundaction)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofiledefaultinboundaction)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofiledefaultoutboundaction)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofiledefaultoutboundaction)
+ +
+
+
+
+
-  Enables Windows Firewall logging for Domain, Private and Public profiles, sets the log file size for each of them to the max `32.767 MB`. Defines separate log files for each of the firewall profiles. Logs only dropped packets for Private and Public profiles, Logs both dropped and successful packets for Domain profile.
Enables Windows Firewall logging for Domain, Private and Public profiles, sets the log file size for each of them to the max `32.767 MB`. Defines separate log files for each of the firewall profiles. Logs only dropped packets for Private and Public profiles, Logs both dropped and successful packets for Domain profile.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofileenablelogdroppedpackets)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofileenablelogdroppedpackets)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofilelogfilepath)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofilelogfilepath)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofilelogmaxfilesize)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoredomainprofilelogmaxfilesize)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofileenablelogdroppedpackets)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofileenablelogdroppedpackets)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofilelogfilepath)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofilelogfilepath)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofilelogmaxfilesize)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstoreprivateprofilelogmaxfilesize)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofileenablelogdroppedpackets)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofileenablelogdroppedpackets)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofilelogfilepath)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofilelogfilepath)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofilelogmaxfilesize)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/firewall-csp#mdmstorepublicprofilelogmaxfilesize)
+ +
+
+
+
+
-  Disables [Multicast DNS (mDNS) UDP-in Firewall Rules for all 3 Firewall profiles](https://techcommunity.microsoft.com/t5/networking-blog/mdns-in-the-enterprise/ba-p/3275777), This might interfere with Miracast screen sharing, which relies on the Public profile, and homes where the Private profile is not selected, but it does add an extra measure of security in public places, like a coffee shop.
- The domain name `.local` which is used in mDNS (Multicast DNS) [is a special-use domain name reserved by the Internet Engineering Task Force (IETF)](https://en.wikipedia.org/wiki/.local) so that it may not be installed as a top-level domain in the Domain Name System (DNS) of the Internet.
@@ -699,6 +1045,10 @@ NistP384
- [Microsoft Defender Application Guard](https://learn.microsoft.com/en-us/windows/security/application-security/application-isolation/microsoft-defender-application-guard/md-app-guard-overview), it's [deprecated](https://learn.microsoft.com/en-us/windows/whats-new/deprecated-features#deprecated-features). Learn more about [Microsoft Edge Security Features here](https://edgestatic.azureedge.net/shared/cms/pdfs/Microsoft_Edge_Security_Whitepaper_v2.pdf).
+
Disables [Multicast DNS (mDNS) UDP-in Firewall Rules for all 3 Firewall profiles](https://techcommunity.microsoft.com/t5/networking-blog/mdns-in-the-enterprise/ba-p/3275777), This might interfere with Miracast screen sharing, which relies on the Public profile, and homes where the Private profile is not selected, but it does add an extra measure of security in public places, like a coffee shop.
- The domain name `.local` which is used in mDNS (Multicast DNS) [is a special-use domain name reserved by the Internet Engineering Task Force (IETF)](https://en.wikipedia.org/wiki/.local) so that it may not be installed as a top-level domain in the Domain Name System (DNS) of the Internet.
@@ -699,6 +1045,10 @@ NistP384
- [Microsoft Defender Application Guard](https://learn.microsoft.com/en-us/windows/security/application-security/application-isolation/microsoft-defender-application-guard/md-app-guard-overview), it's [deprecated](https://learn.microsoft.com/en-us/windows/whats-new/deprecated-features#deprecated-features). Learn more about [Microsoft Edge Security Features here](https://edgestatic.azureedge.net/shared/cms/pdfs/Microsoft_Edge_Security_Whitepaper_v2.pdf).
+ +
+
+
+
+
-  [Uninstalls](https://learn.microsoft.com/en-us/powershell/module/dism/remove-windowscapability) these optional features (Windows Settings -> Apps -> Optional Features):
- Notepad (system): legacy Notepad program. Windows 11 has multi-tabbed modern Notepad app.
@@ -715,6 +1065,10 @@ NistP384
- Steps Recorder: it's [deprecated](https://prod.support.services.microsoft.com/en-us/windows/steps-recorder-deprecation-a64888d7-8482-4965-8ce3-25fb004e975f).
+
[Uninstalls](https://learn.microsoft.com/en-us/powershell/module/dism/remove-windowscapability) these optional features (Windows Settings -> Apps -> Optional Features):
- Notepad (system): legacy Notepad program. Windows 11 has multi-tabbed modern Notepad app.
@@ -715,6 +1065,10 @@ NistP384
- Steps Recorder: it's [deprecated](https://prod.support.services.microsoft.com/en-us/windows/steps-recorder-deprecation-a64888d7-8482-4965-8ce3-25fb004e975f).
+ +
+
+
+
+
-  [Enables](https://learn.microsoft.com/en-us/powershell/module/dism/enable-windowsoptionalfeature) these optional features (Control Panel):
- [Windows Sandbox](https://learn.microsoft.com/en-us/windows/security/application-security/application-isolation/windows-sandbox/windows-sandbox-overview): install, test and use programs in a disposable virtual operation system, completely separate from your main OS
@@ -737,16 +1091,40 @@ NistP384
-
[Enables](https://learn.microsoft.com/en-us/powershell/module/dism/enable-windowsoptionalfeature) these optional features (Control Panel):
- [Windows Sandbox](https://learn.microsoft.com/en-us/windows/security/application-security/application-isolation/windows-sandbox/windows-sandbox-overview): install, test and use programs in a disposable virtual operation system, completely separate from your main OS
@@ -737,16 +1091,40 @@ NistP384
-  [Disables NetBIOS over TCP/IP](https://learn.microsoft.com/en-us/windows-hardware/customize/desktop/unattend/microsoft-windows-netbt-interfaces-interface-netbiosoptions) on all network interfaces.
+
[Disables NetBIOS over TCP/IP](https://learn.microsoft.com/en-us/windows-hardware/customize/desktop/unattend/microsoft-windows-netbt-interfaces-interface-netbiosoptions) on all network interfaces.
+ +
+
+
+
+
-  Disables Smart Multi-Homed Name Resolution because it uses NetBIOS and LLMNR, [protocols that shouldn't be used](https://techcommunity.microsoft.com/t5/networking-blog/aligning-on-mdns-ramping-down-netbios-name-resolution-and-llmnr/bc-p/3644260/highlight/true#M515) anymore.
Disables Smart Multi-Homed Name Resolution because it uses NetBIOS and LLMNR, [protocols that shouldn't be used](https://techcommunity.microsoft.com/t5/networking-blog/aligning-on-mdns-ramping-down-netbios-name-resolution-and-llmnr/bc-p/3644260/highlight/true#M515) anymore.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-dnsclient#dns_smartmultihomednameresolution)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-dnsclient#dns_smartmultihomednameresolution)
+ +
+
+
+
+
-  Disables [LMHOSTS lookup protocol](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-nbte/bec3913a-c359-4e6f-8c7e-40c2f43f546b#gt_5f0744c1-5105-4e4a-b71c-b9c7ecaed910) on all network adapters, legacy feature that's not used anymore.
+
Disables [LMHOSTS lookup protocol](https://learn.microsoft.com/en-us/openspecs/windows_protocols/ms-nbte/bec3913a-c359-4e6f-8c7e-40c2f43f546b#gt_5f0744c1-5105-4e4a-b71c-b9c7ecaed910) on all network adapters, legacy feature that's not used anymore.
+ +
+
+
+
+
-  Sets the Network Location of all connections to Public; [Public network means less trust to other network devices](https://support.microsoft.com/en-us/windows/make-a-wi-fi-network-public-or-private-in-windows-0460117d-8d3e-a7ac-f003-7a0da607448d).
+
Sets the Network Location of all connections to Public; [Public network means less trust to other network devices](https://support.microsoft.com/en-us/windows/make-a-wi-fi-network-public-or-private-in-windows-0460117d-8d3e-a7ac-f003-7a0da607448d).
+ +
+
+
+
+
-  Disables [Printing over HTTP](https://learn.microsoft.com/en-us/troubleshoot/windows-server/printing/manage-connect-printers-use-web-browser) because HTTP is not encrypted and it's an old feature that's not used anymore.
Disables [Printing over HTTP](https://learn.microsoft.com/en-us/troubleshoot/windows-server/printing/manage-connect-printers-use-web-browser) because HTTP is not encrypted and it's an old feature that's not used anymore.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-connectivity?WT.mc_id=Portal-fx#diableprintingoverhttp)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-connectivity?WT.mc_id=Portal-fx#diableprintingoverhttp)
+ +
+
+
+
+
-  Clears all the entries in [Remotely accessible registry paths](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-access-remotely-accessible-registry-paths).
+
Clears all the entries in [Remotely accessible registry paths](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-access-remotely-accessible-registry-paths).
+ +
+
+
+
+
-  Clears all the entries in [Remotely accessible registry paths and subpaths](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-access-remotely-accessible-registry-paths-and-subpaths).
Clears all the entries in [Remotely accessible registry paths and subpaths](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/network-access-remotely-accessible-registry-paths-and-subpaths).
💡 (back to categories)
@@ -767,25 +1145,61 @@ NistP384
- By being launched first by the kernel, ELAM is ensured to be launched before any third-party software and is therefore able to detect malware in the boot process and prevent it from initializing. ELAM drivers must be specially signed by Microsoft to ensure they are started by the Windows kernel early in the boot process.
+ +
+
+
+
+
-  Disables location services (Location, Windows Location Provider, Location Scripting) system wide. Websites and apps won't be able to use your precise location, however they will still be able to detect your location using your IP address.
Disables location services (Location, Windows Location Provider, Location Scripting) system wide. Websites and apps won't be able to use your precise location, however they will still be able to detect your location using your IP address.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-System?WT.mc_id=Portal-fx#allowlocation)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-System?WT.mc_id=Portal-fx#allowlocation)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-locationprovideradm#disablewindowslocationprovider_1)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-locationprovideradm#disablewindowslocationprovider_1)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-sensors#disablelocationscripting_2)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-sensors#disablelocationscripting_2)
+ +
+
+
+
+
-  Enables `svchost.exe` mitigations. built-in system services hosted in `svchost.exe` processes will have stricter security policies enabled on them. These stricter security policies include a policy requiring all binaries loaded in these processes to be signed by Microsoft, and a policy disallowing dynamically generated code.
Enables `svchost.exe` mitigations. built-in system services hosted in `svchost.exe` processes will have stricter security policies enabled on them. These stricter security policies include a policy requiring all binaries loaded in these processes to be signed by Microsoft, and a policy disallowing dynamically generated code.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-servicecontrolmanager)
- Requires Business Windows licenses. e.g., [Windows 11 pro for Workstations](https://www.microsoft.com/en-us/windows/business/windows-11-pro-workstations), [Enterprise](https://www.microsoft.com/en-us/microsoft-365/windows/windows-11-enterprise) or [Education](https://www.microsoft.com/en-us/education/products/windows).
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-servicecontrolmanager)
- Requires Business Windows licenses. e.g., [Windows 11 pro for Workstations](https://www.microsoft.com/en-us/windows/business/windows-11-pro-workstations), [Enterprise](https://www.microsoft.com/en-us/microsoft-365/windows/windows-11-enterprise) or [Education](https://www.microsoft.com/en-us/education/products/windows).
+ +
+
+
+
+
-  Turns on Enhanced mode search for Windows indexer. The default is classic mode.
Turns on Enhanced mode search for Windows indexer. The default is classic mode.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-search#allowfindmyfiles)
- This causes some UI elements in the search settings in Windows settings to become unavailable for Standard user accounts to view, because it will be a managed feature by an Administrator.
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-search#allowfindmyfiles)
- This causes some UI elements in the search settings in Windows settings to become unavailable for Standard user accounts to view, because it will be a managed feature by an Administrator.
+ +
+
+
+
+
-  [Enforce the Administrator role for adding printer drivers](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/devices-prevent-users-from-installing-printer-drivers)
[Enforce the Administrator role for adding printer drivers](https://learn.microsoft.com/en-us/windows/security/threat-protection/security-policy-settings/devices-prevent-users-from-installing-printer-drivers)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#devices_preventusersfrominstallingprinterdriverswhenconnectingtosharedprinters)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#devices_preventusersfrominstallingprinterdriverswhenconnectingtosharedprinters)
+ +
+
+
+
+
-  Enables [SMB/LDAP Signing](https://techcommunity.microsoft.com/t5/storage-at-microsoft/configure-smb-signing-with-confidence/ba-p/2418102)
Enables [SMB/LDAP Signing](https://techcommunity.microsoft.com/t5/storage-at-microsoft/configure-smb-signing-with-confidence/ba-p/2418102)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#microsoftnetworkclient_digitallysigncommunicationsalways)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#microsoftnetworkclient_digitallysigncommunicationsalways)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#microsoftnetworkserver_digitallysigncommunicationsalways)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-LocalPoliciesSecurityOptions?WT.mc_id=Portal-fx#microsoftnetworkserver_digitallysigncommunicationsalways)
+ +
+
+
+
+
-  Enables [SMB Encryption](https://learn.microsoft.com/en-us/windows-server/storage/file-server/smb-security). Its status can be checked using the following PowerShell command: `(get-SmbServerConfiguration).EncryptData`. If the returned value is `$True` then SMB Encryption is turned on.
+
Enables [SMB Encryption](https://learn.microsoft.com/en-us/windows-server/storage/file-server/smb-security). Its status can be checked using the following PowerShell command: `(get-SmbServerConfiguration).EncryptData`. If the returned value is `$True` then SMB Encryption is turned on.
+ +
+
+
+
+
-  Enables Edge browser (stable/beta/dev channels) to download and install updates on any network, metered or not; because the updates are important and should not be suppressed.
+
Enables Edge browser (stable/beta/dev channels) to download and install updates on any network, metered or not; because the updates are important and should not be suppressed.
+ +
+
+
+
+
-  [Enables all Windows users to use Hyper-V and Windows Sandbox](https://learn.microsoft.com/en-us/archive/blogs/virtual_pc_guy/why-do-you-have-to-elevate-powershell-to-use-hyper-v-cmdlets) by adding all Windows users to the "Hyper-V Administrators" security group using its [SID](https://learn.microsoft.com/en-us/windows/win32/secauthz/well-known-sids). By default, only Administrators can use Hyper-V or Windows Sandbox.
+
[Enables all Windows users to use Hyper-V and Windows Sandbox](https://learn.microsoft.com/en-us/archive/blogs/virtual_pc_guy/why-do-you-have-to-elevate-powershell-to-use-hyper-v-cmdlets) by adding all Windows users to the "Hyper-V Administrators" security group using its [SID](https://learn.microsoft.com/en-us/windows/win32/secauthz/well-known-sids). By default, only Administrators can use Hyper-V or Windows Sandbox.
+ +
+
+
+
+
-  Creates custom views for [Windows Event Viewer](https://learn.microsoft.com/en-us/shows/inside/event-viewer) to help keep tabs on important security events:
- [Attack Surface Reduction Rules](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/overview-attack-surface-reduction?view=o365-worldwide#xml-for-attack-surface-reduction-rule-events)
@@ -814,12 +1228,28 @@ NistP384
- USB storage Connects & Disconnects (Flash drives, phones etc.)
+
Creates custom views for [Windows Event Viewer](https://learn.microsoft.com/en-us/shows/inside/event-viewer) to help keep tabs on important security events:
- [Attack Surface Reduction Rules](https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/overview-attack-surface-reduction?view=o365-worldwide#xml-for-attack-surface-reduction-rule-events)
@@ -814,12 +1228,28 @@ NistP384
- USB storage Connects & Disconnects (Flash drives, phones etc.)
+ +
+
+
+
+
-  Enables **WinVerifyTrust Signature Validation**, [a security feature related to WinVerifyTrust function that handles Windows Authenticode signature verification for portable executable (PE) files.](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2013-3900)
+
Enables **WinVerifyTrust Signature Validation**, [a security feature related to WinVerifyTrust function that handles Windows Authenticode signature verification for portable executable (PE) files.](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2013-3900)
+ +
+
+
+
+
-  Enables [Command line process auditing](https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/component-updates/command-line-process-auditing)
Enables [Command line process auditing](https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/manage/component-updates/command-line-process-auditing)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-auditsettings#includecmdline)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-auditsettings#includecmdline)
+ +
+
+
+
+
-  Enables the RPC Endpoint Mapper Client Authentication policy
Enables the RPC Endpoint Mapper Client Authentication policy  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-remoteprocedurecall#rpcendpointmapperclientauthentication)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-remoteprocedurecall#rpcendpointmapperclientauthentication)
+ +
+
+
+
+
-  Enables a policy that requests claims and compound authentication for Dynamic Access Control and Kerberos armoring.
Enables a policy that requests claims and compound authentication for Dynamic Access Control and Kerberos armoring.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-kerberos#kerberosclientsupportsclaimscompoundarmor)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-kerberos#kerberosclientsupportsclaimscompoundarmor)
💡 (back to categories)
@@ -844,13 +1274,51 @@ In Windows by default, devices will scan daily, automatically download and insta
-  Enables [Windows Update to download and install updates on any network](https://techcommunity.microsoft.com/t5/windows-it-pro-blog/the-windows-update-policies-you-should-set-and-why/ba-p/3270914), metered or not; because the updates are important and should not be suppressed, **that's what bad actors would want.**
Enables [Windows Update to download and install updates on any network](https://techcommunity.microsoft.com/t5/windows-it-pro-blog/the-windows-update-policies-you-should-set-and-why/ba-p/3270914), metered or not; because the updates are important and should not be suppressed, **that's what bad actors would want.**  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautowindowsupdatedownloadovermeterednetwork)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautowindowsupdatedownloadovermeterednetwork)
+ +
+
+
+
+
-  Enables "Receive Updates for other Microsoft products" (such as PowerShell)
+
Enables "Receive Updates for other Microsoft products" (such as PowerShell)
+ +
+
+
+
+
-  Enables "Notify me when a restart is required to finish updating"
Enables "Notify me when a restart is required to finish updating"  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#schedulerestartwarning)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#schedulerestartwarning)
--  Sets the grace period for auto restart to 1 day.
Sets the grace period for auto restart to 1 day.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiod)
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiod)  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiodforfeatureupdates)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiodforfeatureupdates)
+ +
+
+
+
+
+-  Specifies the number of days before quality updates are installed on devices automatically to 1 day.
Specifies the number of days before quality updates are installed on devices automatically to 1 day.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforqualityupdates)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforqualityupdates)
+
+ +
+
+
+
+
+-  Specifies the number of days before feature updates are installed on devices automatically to 1 day.
Specifies the number of days before feature updates are installed on devices automatically to 1 day.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforfeatureupdates)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinenoautorebootforfeatureupdates)
+
+ +
+
+
+
+
+-  Sets the number of grace period days before feature updates are installed on devices automatically to 1 day.
Sets the number of grace period days before feature updates are installed on devices automatically to 1 day.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiodforfeatureupdates)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiodforfeatureupdates)
+
+ +
+
+
+
+
+-  Sets the number of grace period days before quality updates are installed on devices automatically to 1 day.
Sets the number of grace period days before quality updates are installed on devices automatically to 1 day.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiod)
--
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#configuredeadlinegraceperiod)
--  Configures the [automatic updates to happen every day](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate), automatically be downloaded and installed, notify users for restart.
Configures the [automatic updates to happen every day](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate), automatically be downloaded and installed, notify users for restart.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate)
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate)
+ +
+
+
+
+
+-  Configures the automatic updates to happen every day, automatically be downloaded and installed, notify users for restart.
Configures the automatic updates to happen every day, automatically be downloaded and installed, notify users for restart.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate)
+
+
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update#allowautoupdate)
+
+ +
+
+
+
-  [Enables features introduced via servicing that are off by default](https://learn.microsoft.com/en-us/windows/deployment/update/waas-configure-wufb) so that users will be able to get new features after having Windows Update settings managed by Group Policy as the result of running this category.
[Enables features introduced via servicing that are off by default](https://learn.microsoft.com/en-us/windows/deployment/update/waas-configure-wufb) so that users will be able to get new features after having Windows Update settings managed by Group Policy as the result of running this category.  [CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update?toc=%2Fwindows%2Fdeployment%2Ftoc.json&bc=%2Fwindows%2Fdeployment%2Fbreadcrumb%2Ftoc.json#allowtemporaryenterprisefeaturecontrol)
@@ -869,16 +1337,63 @@ In Windows by default, devices will scan daily, automatically download and insta
[CSP](https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-update?toc=%2Fwindows%2Fdeployment%2Ftoc.json&bc=%2Fwindows%2Fdeployment%2Fbreadcrumb%2Ftoc.json#allowtemporaryenterprisefeaturecontrol)
@@ -869,16 +1337,63 @@ In Windows by default, devices will scan daily, automatically download and insta
-  [Block 3rd party cookies](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#blockthirdpartycookies) - Recommendatory policy
+
+
[Block 3rd party cookies](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#blockthirdpartycookies) - Recommendatory policy
+
+ +
+
+
+
+
-  [Set Edge to use system's DNS over HTTPS](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#control-the-mode-of-dns-over-https)
+
+
[Set Edge to use system's DNS over HTTPS](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#control-the-mode-of-dns-over-https)
+
+ +
+
+
+
+
-  [Automatic HTTPS upgrade of HTTP connections](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#configure-automatic-https)
+
+
[Automatic HTTPS upgrade of HTTP connections](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#configure-automatic-https)
+
+ +
+
+
+
+
-  [Enable Encrypted Client Hello](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#encryptedclienthelloenabled)
+
+
[Enable Encrypted Client Hello](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#encryptedclienthelloenabled)
+
+ +
+
+
+
+
-  [Disable Basic HTTP authentication scheme](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#basicauthoverhttpenabled)
+
+
[Disable Basic HTTP authentication scheme](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#basicauthoverhttpenabled)
+
+ +
+
+
+
+
-  [Allow devices using this hardening category to receive new features and experimentations like normal devices](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#control-communication-with-the-experimentation-and-configuration-service)
+
+
[Allow devices using this hardening category to receive new features and experimentations like normal devices](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#control-communication-with-the-experimentation-and-configuration-service)
+
+ +
+
+
+
+
-  [Enforce the audio process to run sandboxed](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#allow-the-audio-sandbox-to-run)
+
+
[Enforce the audio process to run sandboxed](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#allow-the-audio-sandbox-to-run)
+
+ +
+
+
+
+
-  [Sets the share additional operating system region setting to never](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#set-the-default-share-additional-operating-system-region-setting) - Recommendatory policy
+
+
[Sets the share additional operating system region setting to never](https://learn.microsoft.com/en-us/deployedge/microsoft-edge-policies#set-the-default-share-additional-operating-system-region-setting) - Recommendatory policy
+
+ +
+
+
+
+
-  [Disables the following weak Cipher Suites](https://learn.microsoft.com/en-us/DeployEdge/microsoft-edge-policies#tlsciphersuitedenylist)
+
- [Site 1 to test TLS in your browser](https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html)
+
- [Site 2 to test TLS in your browser](https://browserleaks.com/tls)
+
+
[Disables the following weak Cipher Suites](https://learn.microsoft.com/en-us/DeployEdge/microsoft-edge-policies#tlsciphersuitedenylist)
+
- [Site 1 to test TLS in your browser](https://clienttest.ssllabs.com:8443/ssltest/viewMyClient.html)
+
- [Site 2 to test TLS in your browser](https://browserleaks.com/tls)
+
+ +
+
+
+
+
-  [CSP](https://learn.microsoft.com/en-us/deployedge/configure-edge-with-mdm)
```
@@ -967,6 +1482,10 @@ This policy defends the system from malware that can launch itself automatically
The WDAC policy employs a wildcard pattern to prevent any file from running in the Downloads folder. Additionally, it verifies that the system downloads folder in the user directory matches the downloads folder in the Edge browser's settings. If there is a discrepancy, a warning message is displayed on the console.
+
[CSP](https://learn.microsoft.com/en-us/deployedge/configure-edge-with-mdm)
```
@@ -967,6 +1482,10 @@ This policy defends the system from malware that can launch itself automatically
The WDAC policy employs a wildcard pattern to prevent any file from running in the Downloads folder. Additionally, it verifies that the system downloads folder in the user directory matches the downloads folder in the Edge browser's settings. If there is a discrepancy, a warning message is displayed on the console.
+ +
+
+
+
+

 Creates a custom [WDAC](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction) policy that blocks the execution of the following executables:
* wscript.exe
@@ -996,13 +1515,53 @@ All of the policies can be easily removed using the [**Unprotect-WindowsSecurity
You don't need Admin privileges to run this category, because no system-wide changes is made. Changes in this category only apply to the current user account that is running the PowerShell session.
-
Creates a custom [WDAC](https://github.com/HotCakeX/Harden-Windows-Security/wiki/Introduction) policy that blocks the execution of the following executables:
* wscript.exe
@@ -996,13 +1515,53 @@ All of the policies can be easily removed using the [**Unprotect-WindowsSecurity
You don't need Admin privileges to run this category, because no system-wide changes is made. Changes in this category only apply to the current user account that is running the PowerShell session.
-  Shows known file extensions in File explorer
+
+
Shows known file extensions in File explorer
+
+ +
+
+
+
+
-  Shows hidden files, folders and drives (toggles the control panel folder options item)
+
+
Shows hidden files, folders and drives (toggles the control panel folder options item)
+
+ +
+
+
+
+
-  Disables websites accessing local language list - good for privacy
+
+
Disables websites accessing local language list - good for privacy
+
+ +
+
+
+
+
-  Turns off safe search in Windows search, will enable +18 content to appear in searches; essentially toggles the button in: Windows settings > privacy and security > search permissions > safe search
--
Turns off safe search in Windows search, will enable +18 content to appear in searches; essentially toggles the button in: Windows settings > privacy and security > search permissions > safe search
-- 
 Enables Clipboard History and sync with Microsoft Account
+
+
Enables Clipboard History and sync with Microsoft Account
+
+ +
+
+
+
+
+-  Enables Clipboard History
+
+
Enables Clipboard History
+
+ +
+
+
+
+
-  Turns on text suggestions when typing on the physical keyboard
+
+
Turns on text suggestions when typing on the physical keyboard
+
+ +
+
+
+
+
-  Turns on "Multilingual text suggestions" for the current user, toggles the option in Windows settings
+
+
Turns on "Multilingual text suggestions" for the current user, toggles the option in Windows settings
+
+ +
+
+
+
+
-  Turns off sticky key shortcut of pressing shift key 5 times fast
+
+
Turns off sticky key shortcut of pressing shift key 5 times fast
+
+ +
+
+
+
+
-  Disables Show reminders and incoming VoIP calls on the lock screen
Disables Show reminders and incoming VoIP calls on the lock screen
💡 (back to categories)
diff --git "a/Wiki posts/Harden\342\200\220Windows\342\200\220Security\342\200\220Module/Harden\342\200\220Windows\342\200\220Security\342\200\220Module.md" "b/Wiki posts/Harden\342\200\220Windows\342\200\220Security\342\200\220Module/Harden\342\200\220Windows\342\200\220Security\342\200\220Module.md"
index fead65ade..bdcc0bf38 100644
--- "a/Wiki posts/Harden\342\200\220Windows\342\200\220Security\342\200\220Module/Harden\342\200\220Windows\342\200\220Security\342\200\220Module.md"
+++ "b/Wiki posts/Harden\342\200\220Windows\342\200\220Security\342\200\220Module/Harden\342\200\220Windows\342\200\220Security\342\200\220Module.md"
@@ -316,7 +316,6 @@ The path to the 'Microsoft 365 Apps for Enterprise zip'. Make sure it's in the z
|UAC_OnlyElevateSigned | Only elevate signed and validated executables | UserAccountControl |
|CountryIPBlocking_OFAC | Include the IP ranges of OFAC Sanctioned Countries in the firewall block rules | CountryIPBlocking |
| DangerousScriptHostsBlocking | Deploys the Dangerous Script Hosts Blocking WDAC Policy | DownloadsDefenseMeasures |
-| ClipboardSync | Enables Clipboard Sync with Microsoft Account | NonAdminCommands |



