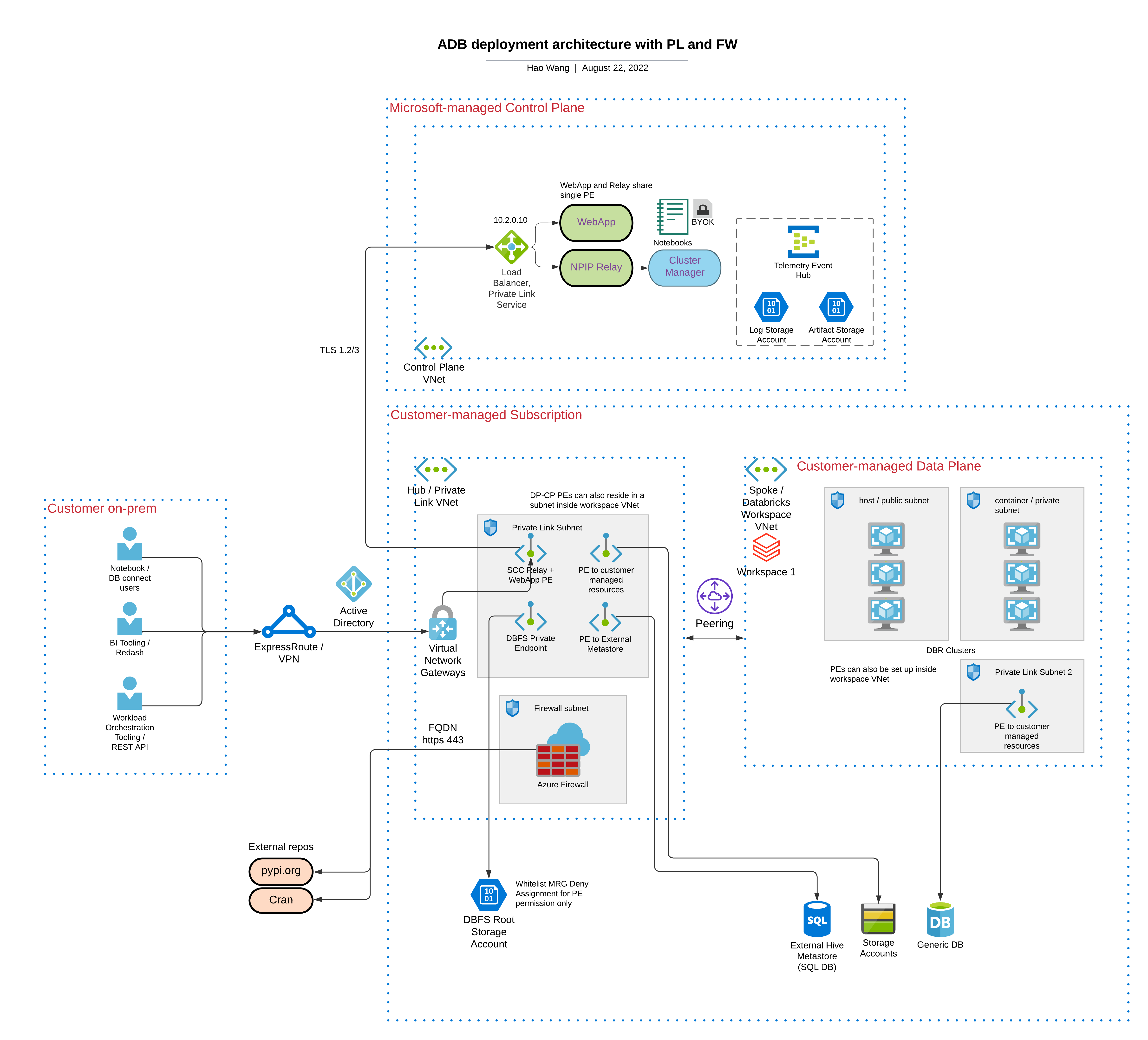
Azure Databricks with Private Links and Hub-Spoke Firewall structure (data exfiltration protection).
Include:
- Hub-Spoke networking with egress firewall to control all outbound traffic, e.g. to pypi.org.
- Private Link connection for backend traffic from data plane to control plane.
- Private Link connection from user client to webapp service.
- Private Link connection from data plane to dbfs storage.
With this deployment, traffic from user client to webapp (notebook UI), backend traffic from data plane to control plane will be through private endpoints. This terraform sample will create:
- Resource group with random prefix
- Tags, including
Owner, which is taken fromaz account show --query user - VNet with public and private subnet and subnet to host private endpoints
- Databricks workspace with private link to control plane, user to webapp and private link to dbfs
- Clone this repo to your local machine.
- Run
terraform initto initialize terraform and get provider ready. - Change
terraform.tfvarsvalues to your own values. - Inside the local project folder, run
terraform applyto create the resources.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| hubcidr | n/a | string |
"10.178.0.0/20" | yes |
| spokecidr | n/a | string |
"10.179.0.0/20" | yes |
| no_public_ip | n/a | bool |
true |
yes |
| rglocation | n/a | string |
"southeastasia" | yes |
| metastoreip | n/a | string |
"40.78.233.2" | yes |
| dbfs_prefix | n/a | string |
"dbfs" | yes |
| workspace_prefix | n/a | string |
"adb" | yes |
| firewallfqdn | n/a | list(any) |
fqdn rules | yes |
| Name | Description |
|---|---|
| arm_client_id | n/a |
| arm_subscription_id | n/a |
| arm_tenant_id | n/a |
| azure_region | n/a |
| databricks_azure_workspace_resource_id | n/a |
| resource_group | n/a |
| workspace_url | n/a |