-
Notifications
You must be signed in to change notification settings - Fork 9
3. Validating the Token
Great, we have set up a server! If you have paid attention you might have noticed, however, that everyone can use a simple post to simulate a KPN LoRa message and is able to fake being your device by only knowing the (not-so-secret) DevEUI.
The token is generated with a SHA256 method as outlined by KPN on their forum. Here we will implement a version of SHA256 to do this check.
#Formatting the SHA256 string If you have read the information of KPN you will notice that we need to feed a string containing some post-query parameters plus some information from the body to a SHA256 method.
- Go to your "Catch Parse Input" node and add the below code at the bottom of you're already existing code - one-line above the
return msg;- to create the SHA256 string. Can you read the code and understand what's happening?
//Enter your LRC-AS key below
var LRC_AS_key = "xxxxxxxxxxxxxxxxxxxxxx";
//Read body msg.payload for SHA
msg.body_parameters = body.CustomerID + body.DevEUI + body.FPort + body.FCntUp + body.payload_hex;
//Read query parameters with msg.req.query
msg.query_sha = msg.req.query;
//Store Token to compare
msg.PostToken = msg.req.query.Token;
//Node-Red does not get the + in the ThingPark timestamp correctly and needs to be added
msg.query_sha.Time = msg.query_sha.Time.replace(" ", "+");
// Create a string of query parameters without Token
var query_str = "";
for(var k in msg.query_sha) {
if (k != "Token"){
query_str += k + "=" + msg.query_sha[k] + "&";
}
}
msg.query_str = query_str.slice(0,-1); // Delete last '&' sign in the string
msg.SHA_string_no_key = msg.body_parameters + msg.query_str; // Save a SHA string withouth a key
msg.SHA_string = msg.SHA_string_no_key + LRC_AS_key; // Save a SHA string, including the keyNote that you have to change the LRC_AS_key to match your SHA key from your profile in the Developer Portal or the Application Server profile in the Thingpark deviceManager.
-
Now we would need a SHA256 node, but that does not come prepackaged with NodeRed. Luckily someone made one for us at https://github.com/emn178/js-sha256. The nice way would be to install this library in NodeRed. Installing something in NodeRed will take some time for those of us who don't know how to do this and we want to focus on the LoRa part here. Therefore we will just copy paste the method in a function node and use it there (it's not very big :)):
- Go to the SHA256 github > src to find js-sha256.js https://github.com/emn178/js-sha256/blob/master/src/sha256.js.
- Copy the code to your clipboard. Note when copy-pasting through your browser, please click on the "Raw" button first to correctly copy it.
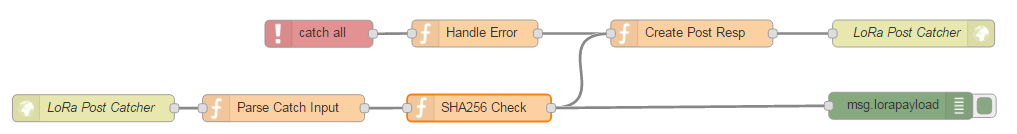
- Add a new function node called "SHA256 check" in your flow directly after "Catch Parse Input" (see below) and paste the code.
- Scroll all the way down in your code to the end of what you have copy-pasted and add the below code.
// The code above is a sha256() function
// Below we do the actual check
var Token = sha256(msg.SHA_string);
if (Token != msg.PostToken) {
// Pass an error with the SHA string (no key!!) back for debugging
node.error("Token did not match on " + msg.SHA_string_no_key, msg);
return;
}
return msg;- Can you see how we did a check and compared the answer? If the answer is not valid we generate an error like we did in exercise 2.
- Now try to use the developer portal or simulate a message through postman to send a test message and see what happens. Note that the LRC-AS-key should be adjusted accordingly in the "Parse Catch Input" node. The examples of the simulator also include the key they should have for this check.
Congratulations! You have already made a nice server to receive uplink data. Instead of sending it to a debug node you have all sorts of tools at your disposal to send the LoRa Payload to. You could, for instance, send it to a database to store it, forward it to a web service, combine it with other datasources, you name it.
If you're still interested you can move on to exercise 4 to learn how to have a bit of interaction outside of NodeRed.
You can find the complete implementation of the exercise at https://github.com/iotacademy/NodeRed_KPN_LoRa/blob/master/03_CheckingSHA.md if you are stuck somewhere.